- Author Jason Gerald gerald@how-what-advice.com.
- Public 2023-12-16 10:50.
- Last modified 2025-01-23 12:04.
Hacking a Gmail address can be useful if you forget your account password. This is also a good way to test the security level of your account. There are several ways you can try to hack Gmail. Almost all ways require you to get someone's password through some other means. Hacking other people's Gmail accounts is illegal.
Step
Method 1 of 4: Setting Expectations
Step 1. Understand the limitations
Gmail is actually a very secure service. The only way you can "hack" someone's account is to steal their password. If your target has two-factor authentication, you'll also need their mobile device. There is no other way to hack two-factor authentication.

Step 2. Understand the legality
Accessing someone else's email account without permission is illegal in most areas. This article is for educational purposes only.
Method 2 of 4: Using Keylogger
Step 1. Find a keylogger program that suits your needs
Keylogger is a program that records the keystrokes of the keyboard (keyboard) on the computer that installs it. There are many free or paid keylogger programs on the internet, which have varying degrees of confidentiality. Make sure you research all the available options carefully. Some of the popular programs include:
- Actual Keylogger
- Spyrix Free Keylogger
- Black Box Express
- KidLogger
- NetBull
- Lola
Step 2. Install the keylogger on the target computer
You need administrator access to log in to the target computer. On most computers, the usual password is "admin" or left blank.
- Depending on the program you use, the process for installing a keylogger may vary.
- Installing a keylogger without the owner knowing is illegal.
Step 3. Start the keylogger service
Start the service for the program to start recording keystrokes. How to do this will vary depending on the program you are using. You may need to first configure the program so that it can record keystrokes if the program has multiple functions.
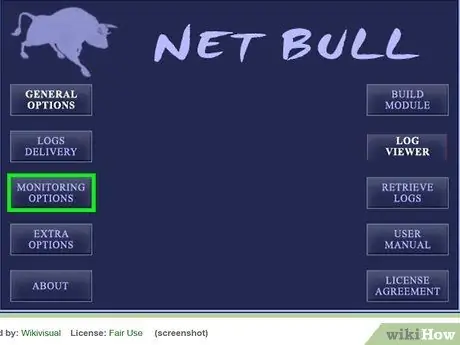
Step 4. Let the keylogger run while the target is using his computer
Most likely the keylogger will capture a lot of information. You can filter it based on the window the target is typing in.
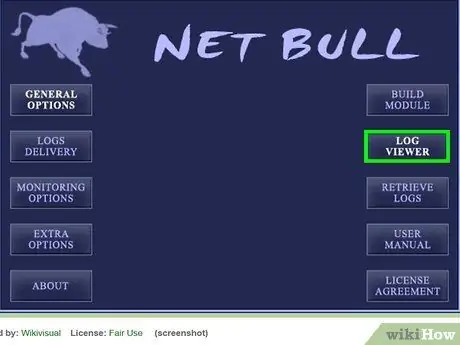
Step 5. View the recorded keystrokes
Some keylogger programs email the recordings to you. Other programs will ask you to export the recordings from the computer on which this program is installed. Go through the records until you find what you think is your target's Gmail password. Maybe you can filter it based on the Gmail login page used by the target..
If the keylogger can't email the recording, you'll need to access the program on the computer it's installed on to view the recording
Method 3 of 4: Using a Browser Password Manager
Step 1. Open the web browser used by your target on their computer
You must be able to access the computer used by the target. Try doing this while they are out of the room or if you have a few minutes in the room without anyone else.
Open a link from the email or the Help menu to start the default browser
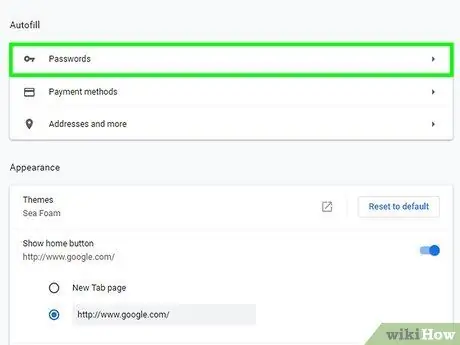
Step 2. Open the password manager
How to open the password manager will vary depending on the browser you are using.
- Internet Explorer - Click the Gear button or the Tools menu and select "Internet Options". Click the "Content" tab and then click the "Settings" button in the AutoComplete section. Then select "Manage Passwords" from the new window.
- Chrome - Click the Chrome Menu button (☰) and select "Settings". Click the "Show advanced settings" link and scroll to the "Passwords and forms" section. Click "Manage passwords".
- Firefox - Click the Firefox Menu button (☰) and select "Options". Click the "Security" tab and then click "Saved Passwords".
- Safari - Click the Safari menu and select "Preferences". Click the "Passwords" tab.
Step 3. Find the password used for the target Google account
Use the search bar in the password manager to search for "google". This is the fastest way to narrow down the password list. Look for the "accounts.google.com" entry to get the target Gmail address.
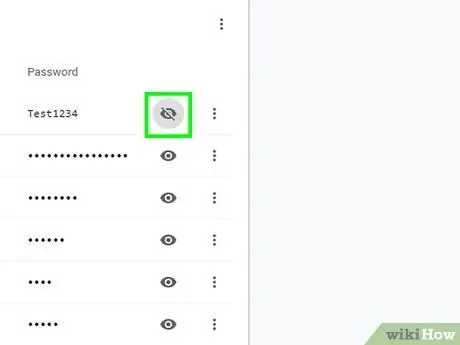
Step 4. Show the password
Select the password and then click the "Show" or "Show Password" button. You may need to enter the administrator password for the computer you are hacking for the password to be displayed.
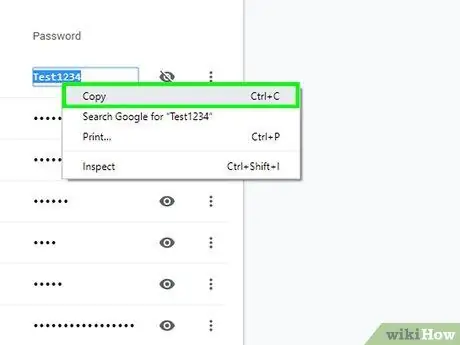
Step 5. Write down the password and then close the password manager
Make a note of the password as well as the target's Gmail address exactly. When you're done, close the password manager to get rid of your tracks.
Step 6. Try the password on another computer
If your target hasn't enabled two-factor authentication, you should be able to access their account. Maybe the target will be notified that someone else is logging into their account from an unknown browser.
When the target has enabled two-factor authentication, you must have a code sent to their mobile device. When it is activated, you will not be able to do anything
Method 4 of 4: Using Packet Sniffer
Step 1. Understand the process
When someone logs into Gmail (or any login service), a file called a "cookie" is sent to that person's computer. These cookies allow these users to stay logged in, even if they have left Gmail. Packet sniffers can find cookies that are sent over a wireless network. If you find a Gmail cookie, you can open it on your computer and it will most likely open the inbox of your target's email. This can be done when you are connected to the same wireless network that your target uses.
- This method will not work if your target has encryption enabled (https://). This is enabled by default in Gmail, so its usefulness is limited.
- The use of packet sniffers on public networks to intercept data traffic is illegal.
Step 2. Download and install Wireshark
Wireshark is a free utility for network monitoring that can be downloaded at wireshark.org. This program is available for Windows, Mac, and Linux. You can install Wireshark easily. Just follow the installation instructions as you would in any other program.
Don't forget to install the Tshark component during installation. This component is required to retrieve cookies over a wireless network. You must also have "WinPcap" installed
Step 3. Download Cookie Cadger
This is a Java program that will find and bypass cookies sent over the wireless network. You do not need to install Cookie Cadger. This program can be run on all operating systems.
You must have Java 7 installed in order to use Cookie Cadger. Download Java from java.com/download. See How to Install Java for more details
Step 4. Connect to the same wireless network your target uses
You must be connected to the same wireless network as your target. So, your position must be close to the target.

Step 5. Run Wireshark
You must run Wireshark for Cookie Cadger to work.
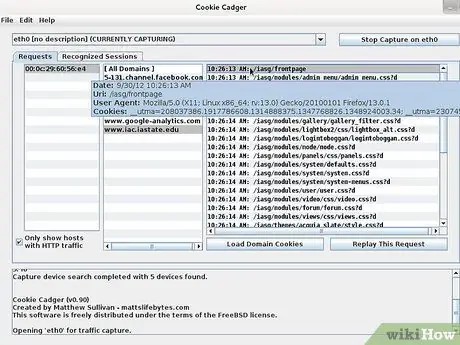
Step 6. Run Cookie Cadger and select your wireless adapter
Select the adapter connected to the wireless network from the drop-down menu. You will see a keyframe containing some insecure cookies from other people using the network.
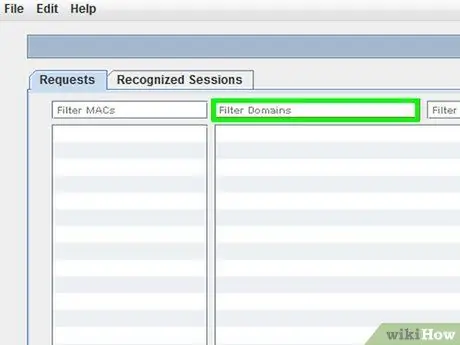
Step 7. Use the domain filter to search for Google cookies
The list of domains found by Cookie Cadger will be displayed in the second column. Look for Google domains, specifically mail.google.com.
Keep in mind that this only works when the target is not using https. If their connection is secure, you won't be able to find their cookies
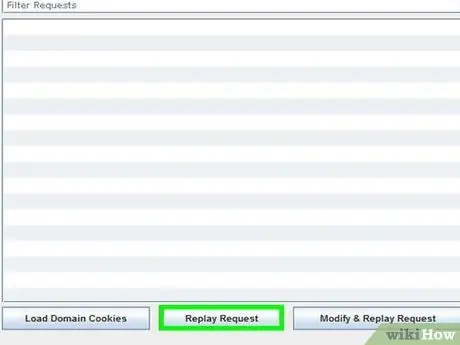
Step 8. Click "Replay This Request" when you have found the Gmail cookie
The cookie will load in your own web browser. The right cookie will take you straight to the target's inbox.
When your target logs out, you won't be able to access their Gmail anymore
Warning
- Beware, many programs claim to be able to hack Gmail accounts, but are actually scams.
- The sole purpose of this article is to provide knowledge and to make people aware of the security of their accounts.






