- Author Jason Gerald gerald@how-what-advice.com.
- Public 2024-01-15 08:07.
- Last modified 2025-01-23 12:04.
Are you a computer expert? Or do you want to be known as an experienced hacker? To hack (hack) a computer, you have to learn computer systems, network security, and codes. Thus, people will be impressed when they see someone who appears to be hacking. You don't have to do anything illegal to make people think you're hacking. Using a basic terminal command or creating a ".bat" file to run a multi-character The Matrix-style browser can take people by surprise.
Step
Method 1 of 3: Using Command Prompt
Step 1. Open the " Run " program on the computer
You can open this program by clicking on the Start menu and searching for the program " Run " in the search field provided on the menu. In addition, you can also search for the program "Run" in Windows Explorer. Usually this program is located in the following location: “C:\Users\[Your Username]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\System Tools“.
Windows users can use hotkeys or shortcuts to open the " Run " program by pressing these two keys: Win+R
Step 2. Open a “Command Prompt” window
You can open this window by typing "Cmd" in the search field available in the "Run" window. This will open a "Command Prompt" window which is also known as the "Command Line". This window is used to control the computer system with text.
Apple users You can use "Spotlight" to search for the Mac version of "Command Prompt" named "Terminal". Type "terminal" in the search field available under "Spotlight".
Step 3. Use “Command Prompt” or “Terminal” to pretend hack
There are many commands that can be used in the " Command Prompt " (for Windows) and "Terminal" (for Apple) to activate commands or get information. The following commands can be used to make you look like an expert hacker without breaking your computer system and breaking the rules.
-
For Windows users, type the commands below and press Enter key to activate them. Type and activate each command quickly to make the hacking process look more complicated:
-
"colora"
This command will change the color of the text contained in the "Command Prompt" window from white to green. The text will be displayed on a black background. Replace the letters in front of the word " color " with the numbers 0 - 9 or the letters A - F to change the color of the Command Prompt letters
- dir
- ipconfig
- tree
-
ping google.com
The command "ping google.com" is used to check if the device (device) can communicate with other devices on the network. In general, people do not know the function of this command. The Google website is used as an example only in this article. You can use any website to enable this command
-
-
If you have an Apple computer, you can use the following safe commands to populate the screen with an interface similar to the interface used by professional hackers. Enter the following text in a Terminal window to display the effect:
- top
- ps -fea
- ls -ltra
Step 4. Activate the command on some Command Prompt or Terminal window
Open several Command Prompt or Terminal windows and activate various commands. By doing this, it will appear that you are doing several complex and unrelated hacking processes at once.
Method 2 of 3: Creating a.bat File on Windows
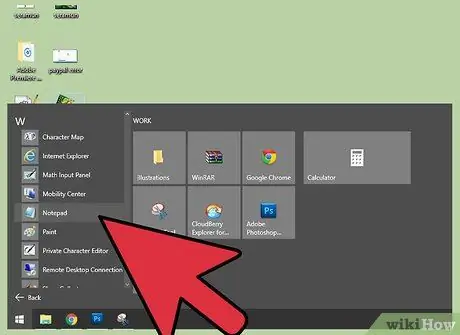
Step 1. Open the Notepad program
To create a ".bat" file, you must write text in a text-editing program and save the file in ".bat" format for the computer to run as an executable program (executable program or programs run by the computer to execute certain instructions or commands). Notepad or another text-editing program can be used to create a ".bat" file.
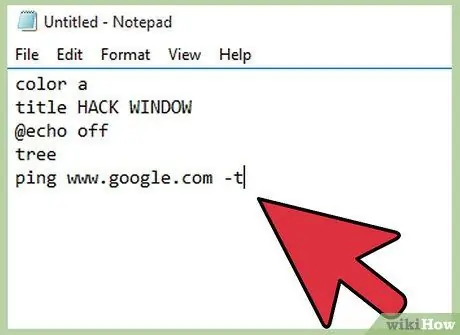
Step 2. Write the command for the ".bat" file in Notepad
The command text written below will open a window called "Hacking Window" and change the font color to green. To change the window title, you can replace the text that is written after " title " with the desired title in Notepad. The text " @echo off " will hide the Command Prompt, while the text " tree " will show the directory tree. This will make the hacking process look more realistic. The last line of text serves to contact Google's servers. Although this is a legal action and is usually done by computer users, ordinary people will see it as a hacking process. Write the following text in an empty Notepad file:
-
color a
title HACK WINDOW
@echo off
tree
ping www.google.com -t
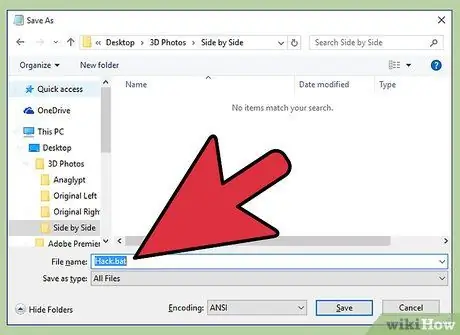
Step 3. Save the file in ".bat" format
When saving the file, you must select the " Save as " option to open the file save window. After that, you can name the file and end the name with a ".bat" extension in the text field provided. This will change the file extension from a text file to a batch file. Batch files contain various commands that can be executed by the computer's operating system.
- This step may not work on Windows Vista.
- You may receive a message that saving the file in ".bat" format will omit the text formatting. Click " Yes " to create a ".bat" file.
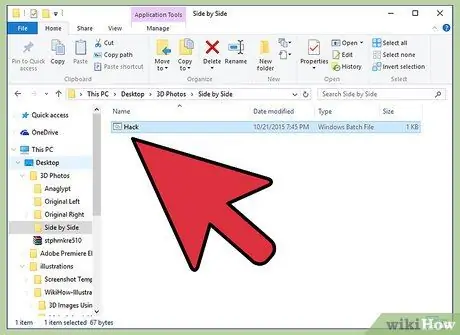
Step 4. Run the ".bat" file
Double-click the ".bat" file stored in the directory. After that, a window showing an interface that mimics the hacking process will appear on the screen.
Method 3 of 3: Using the Website
Step 1. Open a browser (browser)
Some websites provide features that allow visitors to generate images, text, and interfaces that mimic complex commands executed by computers. These features are used to produce movie or video effects. You can also use this website to pretend to be hacking.
Step 2. Go to hackertyper.net
This website generates text that mimics the structure of commands executed by hackers. This text is generated at such a high speed that it can take people by surprise. However, this fast text generation process can make people suspicious of you.
Step 3. Open a separate browser window and visit guihacker.com
After opening this website, keep the browser window open. This window will display images similar to the stereotyped interfaces used by hackers: rows of numbers, rapidly changing interfaces, and fluctuating sine waves. When this website opens and appears on the screen, you can say:
- "I'm compiling data from a friend's server to look for errors in the code, here. The program has to be run for a few hours to make sure all errors are found."
- "I'm opening the analysis program on the monitor so I can see directly the temperature of the processor when I overclock."
Step 4. Choose and use various hacking simulation themes available on geektyper.com
This website provides probably the most realistic hacking simulation. After opening the home page of the website, select the desired theme. After that, type in the text field provided to create a text that is similar to the text generated by the hacker. Also, you can click on the directory to show the fake hacking process which looks complicated.
You can display small windows containing the hack interface and image by clicking on the directory that appears on the screen when you select a theme. Additionally, you can press keyboard keys to create text that mimics the structure of commands created by hackers
Step 5. Open these websites in separate browser windows
Each website has a different hacking text theme and structure. You can quickly switch browser windows by holding down the alt=""Image" key and pressing the Tab key to alternately display open browser windows on the screen. Type some text into each browser window before pressing Alt+Tab key to bring up another browser on the screen. This is done to make you look like an expert hacker. If the website tabs are open in the same browser window, press Ctrl+Tab.
Try designing a layout for each browser window or opening multiple browser windows on the screen to make yourself look like an experienced hacker
Tips
- If you know the commands used to create batch files, you can use them to create more complex hack simulations.
- You can follow the steps listed in this article to impress your friends.
Warning
- People who are good at computer science and programming languages can guess quickly that you're just pretending to be hacking. Therefore, choose your audience of "hacking" action carefully.
- While watching your actions, some adults may think that you are really hacking. Therefore, follow these steps carefully and lest you get into trouble.
- Be careful when using the Command Prompt. Otherwise, you could accidentally run a command that could damage important computer system files. If this file is damaged, the data stored on the computer cannot be accessed again or even lost.






