- Author Jason Gerald gerald@how-what-advice.com.
- Public 2023-12-16 10:50.
- Last modified 2025-06-01 06:05.
If you want to connect to other computers over a notoriously insecure Internet, you may want to do everything you can to keep your data safe. SSH is one way to secure your data. To secure data, you need to properly set up SSH on your computer, then establish an encrypted connection to the server. Keep in mind, though, that in order to establish a secure connection, both connection points must have SSH. Follow this guide to make sure your connection is as secure as possible.
Step
Part 1 of 3: Connecting For The First Time
Step 1. Install SSH
For Windows, you need to download an SSH client. The most popular client is Cygwin, which is available for free from the developer's site. Download and install it like installing any other program. Another free option is PuTTY.
- During Cygwin installation, you must choose to install OpenSSH from the Net section.
- Linux and OS X already have an SSH client on the system, because SSH is a Unix system, and Linux and OS X come from Unix.
Step 2. Run SSH
Open the Terminal program installed by Cygwin, or open a terminal on OS X or Linux. SSH uses a terminal interface to interact with other computers. There is no graphical interface for SSH, so you should be comfortable typing commands.
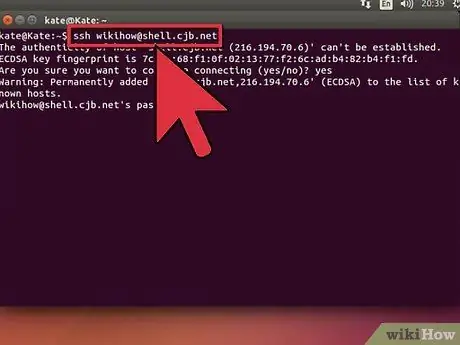
Step 3. Check the connection
Before you generate a security key and move files, you may want to check that SSH is properly configured on your computer and on your target computer. Enter this command, changing it with your username and with the address of your target computer or server.:
-
$ssh@
- You will be asked for a password after a successful connection. You will not see the cursor move or the characters entered as you type your password.
- If this step fails, it may be that SSH is not set up correctly on your computer, or the server is not accepting SSH connections.
Part 2 of 3: Learning Basic Commands
Step 1. Browse to the SSH shell
The first time you connect to a remote computer, you will be in the HOME directory. To move between directory structures, use the command
CD
:
-
cds..
- will move you one directory up.
-
CD
- will move you to the subdirectory you entered.
-
cd /home/directory/path/
- will move you to a specific directory from root (home)
-
cd ~
- will return you to the HOME directory.
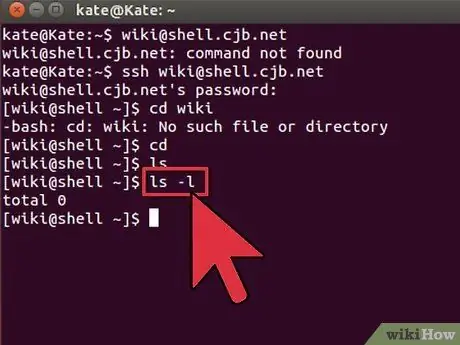
Step 2. Check the contents of the current directory
To view files and folders at your current location, you can use the command
ls
commands:
-
ls
- will show all files and folders in the current directory.
-
ls -l
- will display the contents of the directory along with additional information such as size, permissions, and date.
-
ls-a
- will show the entire directory including hidden files and folders.
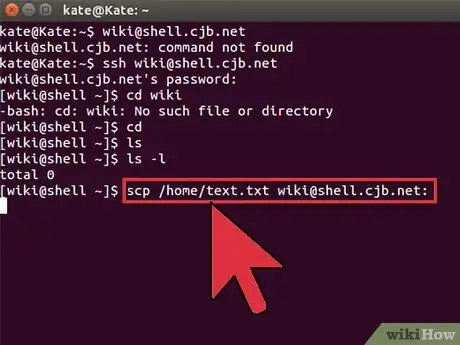
Step 3. Copy the files from your computer to the remote computer
If you need to copy files from your computer to a remote computer, you can use the command
scp
commands:
-
scp /localdirectory/example1.txt @:
- will copy example1.txt to on the remote computer. You can leave blank to copy to the root folder on the remote computer.
-
scp @:/home/example1.txt./
- will move example1.txt from the home directory on the remote computer to the current directory on your computer.
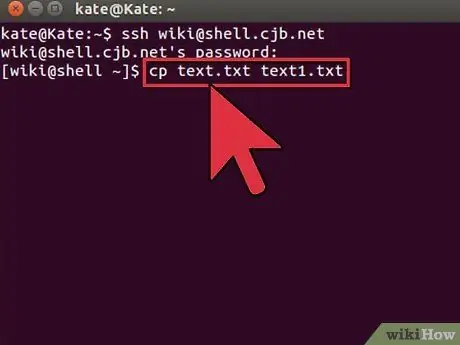
Step 4. Copy the file via the shell
You can use the command
cp
to copy files to the same directory or to a directory of your choice.
-
cp example1.txt example2.txt
- will create a copy of example1.txt named example2.txt in the same location.
-
cp example1.txt /
- will make a copy of example1.txt to the specified location in.
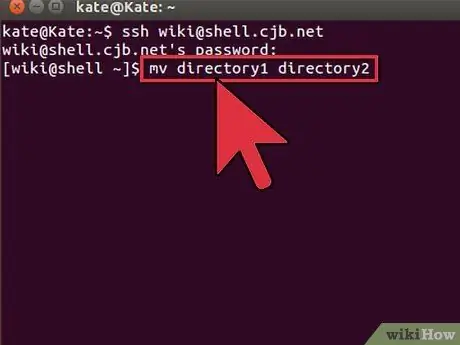
Step 5. Move and rename the file
If you want to rename a file or move it without copying, use the command
mv
-
mv example1.txt example2.txt
- will rename the file example1.txt to example2.txt. The files will be in the same location.
-
mv directory1 directory2
- will rename directory1 to directory2. The contents of the directory will not change.
-
mv example1.txt directory1/
- will move example1.txt to directory1.
-
mv example1.txt directory1/example2.txt
- will move example1.txt to directory1 and rename it to example2.txt
Step 6. Delete files and directories
If you need to delete anything from the remote computer, you can use the command
rm
-
rm example1.txt
- will delete the example1.txt file.
-
rm -I example1.txt
- will delete the example1.txt file after giving you a warning.
-
rm directory1/
- will delete directory1 and all of its contents.
Step 7. Change file permissions
You can change the read and write permissions on your files with the command
chmod
-
chmod u+w example1.txt
will add write/modify file permissions for the user (u). You can also use
g
for group permissions and
o
- for world licensing.
-
chmod g+r example1.txt
- will add read/access permissions on files for the group.
- There is a large list of permissions that you can use to secure or open access to various aspects of your system.
Step 8. Learn other basic commands
There are some other important commands that you will use frequently in the shell interface, as follows:
-
mkdir newdirectory
- will create a new directory with the name newdirectory
-
pwd
- will display your current directory.
-
who
- will display who is currently logged into the system.
-
pico newfile.txt
or
vi newfile.txt
- will create a new file and open the file editor. Different systems will have different file editors. The most common editors are pico and vi. You will need to use a different command if you use a different file editor.
Step 9. Get detailed information for any command
If you are unsure of the function of a command, use the command
man
to learn all the parameters and their uses.
-
man
- will display information regarding the command.
-
man -k
- will search all man pages with the keywords you entered.
Part 3 of 3: Generating an Encrypted Key
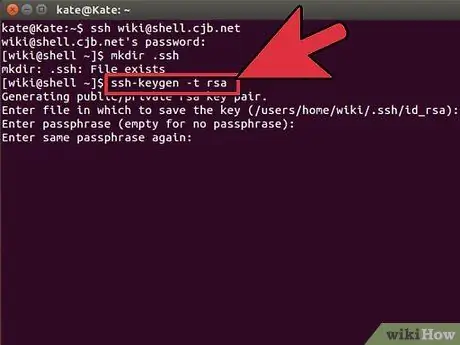
Step 1. Generate an SSH key
This key allows you to connect to a remote location without having to enter a password every time. This will make your connection to the remote computer more secure, as your password will not be sent over the network.
-
Create a key folder on your computer by entering the command
$ mkdir.ssh
-
Generate private and public keys with command
$ ssh-keygen -t rsa
- You will be asked to create a password for the key; it is optional. If you don't want to enter a password for the key, press Enter. This will create two keys in the.ssh folder: id_rsa and id_rsa.pub.
-
Change your private key permissions. To make sure your private key can only be read by you, enter the command
$ chmod 600.ssh/id_rsa
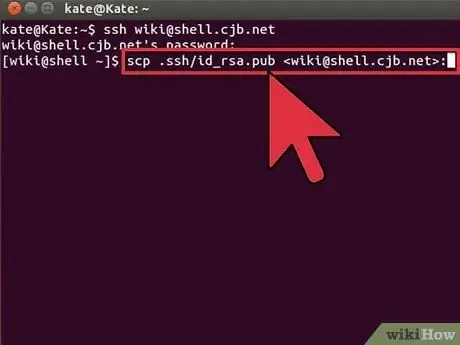
Step 2. Place the public key on the remote computer
After you generate the key, you can store the public key on the remote computer so you can connect without a password. Enter the following command by changing certain parts as described earlier::
-
$ scp.ssh/id_rsa.pub @:
- Make sure you include a colon (:) at the end of the command.
- You will be asked for a password before the transfer process begins.
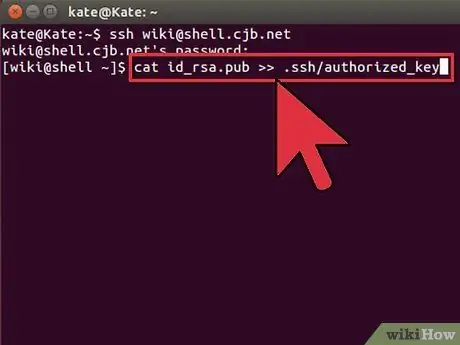
Step 3. Install the public code on the remote computer
Once you have placed the code on the remote computer, you will need to install it for the code to work properly. First, log in to the system in the manner described in step 3.
-
Create an SSH folder on the remote computer if it doesn't already exist:
$ mkdir.ssh
-
Put your key in an authorized key file. If the file does not exist, it will be created.
$ cat id_rsa.pub >>.ssh/authorized_keys
-
Change the permissions for the SSH folder to make it accessible:
$ chmod 700.ssh
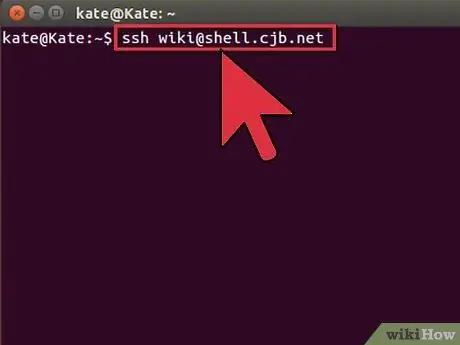
Step 4. Check if the connection is working
Once the key is installed on the remote computer, you should be able to initiate a connection without being asked for a password. Enter this command to check the connection:
$ssh@






