- Author Jason Gerald gerald@how-what-advice.com.
- Public 2024-01-02 02:28.
- Last modified 2025-06-01 06:05.
Are you worried about the security of your network or someone else's network? One of the basics of network security is to make sure your router is protected from intruders. One of the basic tools that can be used to secure it is Nmap or Network Mapper. This program will scan the target and report the open and closed ports. Network security experts use this program to test network security. To learn how to use the program, read this wikiHow article.
Step
Method 1 of 2: Using Zenmap
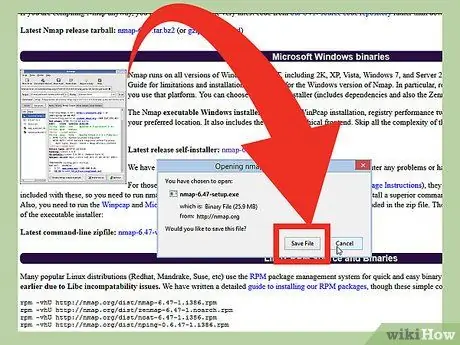
Step 1. Download the Nmap installer file
This file (file) can be obtained for free from the developer website Nmap. It is recommended that you directly download the Nmap installer file from the developer's website to avoid viruses or fake files. The downloaded Nmap installer file contains the Zenmap application. Zenmap is a graphical interface for Nmap that helps novice users to scan their computers without having to learn the command line.
The Zenmap program is available for Windows, Linux, and Mac OS X operating systems. You can find all the installer files for all operating systems on the Nmap website
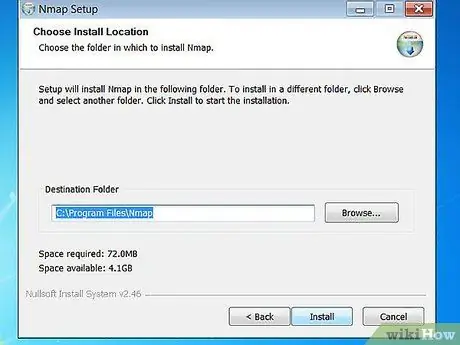
Step 2. Install Nmap
Run the Nmap installer file once it's downloaded. You will be asked to select the program components you want to install. To maximize the performance of Nmap, we recommend that you tick all the options. Nmap will not install adware or spyware.
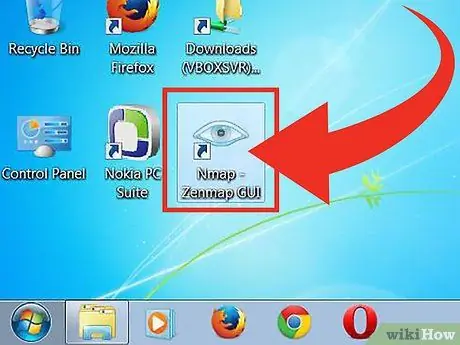
Step 3. Run “Nmap - Zenmap GUI” program
If you use the default option when installing Nmap, you will see the Nmap icon on the desktop. Otherwise, look for this icon in the Start menu. Opening Zenmap will run the program.
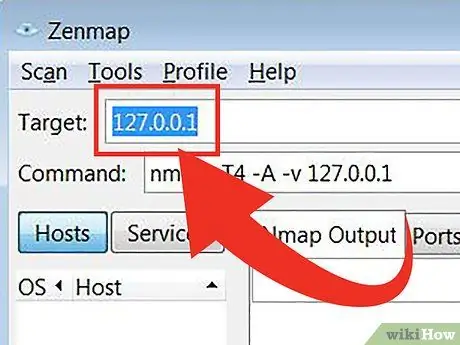
Step 4. Enter the target you want to scan
The Zenmap program makes the scanning process easy. The first step to running a scan is to select a target. You can enter a domain (example.com), IP address (127.0.0.1), network (192.168.1.0/24), or a combination of these targets.
Depending on the intensity and target of the scan, running an Nmap scan may violate the rules set by your internet service provider and could get you into trouble. We recommend that you check local laws and internet service provider contracts before running an Nmap scan on targets originating outside your network
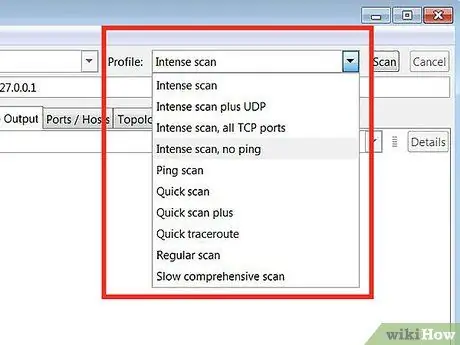
Step 5. Select Profile
A profile is a preset that contains a set of modifiers that define the scan target. This feature allows you to quickly select the type of scan without having to enter a modifier on the command line. Choose a profile that suits your needs:
- Intense scan - Thoroughly performed scans. This profile contains operating system (operating system or OS) detection, version detection, script scanning (script), traceroute, and aggressive scanning time. This option is a scan that could interfere with the system and network.
- Ping scan - This scan is used to detect whether the target has entered the network (online). This option will not scan any ports.
- Quick scan - This scan is faster than regular scan because this option has an aggressive scan time and only scans selected ports.
- Regular scan - This option is a standard Nmap scan without any modifier. This scan will return pings and open ports to the target.
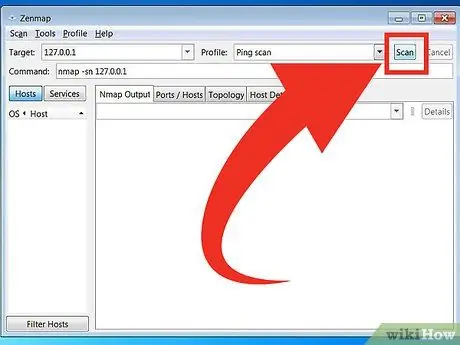
Step 6. Click Scan to start scanning
Scan results will be displayed in real time in the Nmap Output tab. The scan duration varies depending on the selected scan profile, the distance between your computer and the target, and the target network configuration.
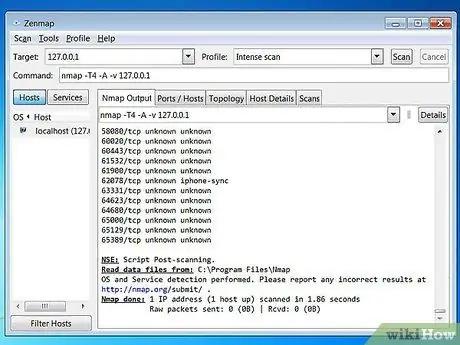
Step 7. View the scan results
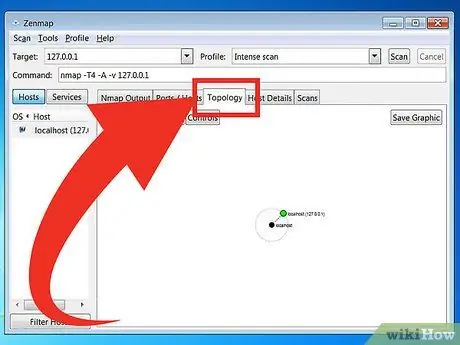
Topology - This tab displays the traceroute for the scan you performed. You can see how many hops (a section of the path that lies between the source and destination of the data) that the data goes through to reach the target.
Host Details - This tab displays a summary of the data obtained from the target scan, such as the number of ports, IP address, hostname (hostname), operating system, and others.
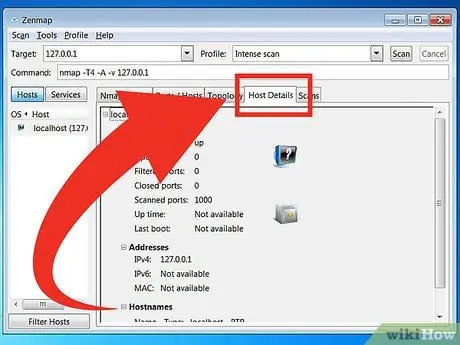
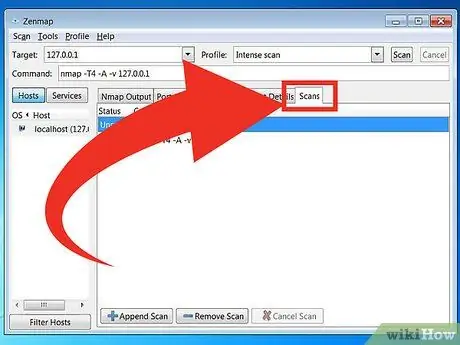
Scans - This tab stores all commands (commands) that were activated in the previous scan. The tabs allow you to quickly rescan targets with a specific set of parameters.
Method 2 of 2: Using the Command Line
Step 1. Install Nmap
Before using Nmap, you must first install it so that you can run it from the operating system command line. The Nmap program is small in size and can be obtained for free from the Nmap developers. Follow the instructions below to install Nmap on your operating system:
-
Linux - Download and install Nmap from your repository. Nmap is available in most major Linux repositories. Enter the following command based on the Linux distribution you have:

Run a Simple Nmap Scan Step 8Bullet1 - For Red Hat, Fedora, and SUSE
- (64-bit)
- For Debian and Ubuntu
rpm -vhU
(32-bit) OR
rpm -vhU
sudo apt-get install nmap
For Windows - Install the Nmap installer file. This file can be obtained for free from the developer's website Nmap. It is recommended that you directly download the Nmap installer file from the developer's website to avoid viruses or fake files. Using the Nmap installer file allows you to quickly install the Nmap command line tool without having to extract the files to the proper folder.
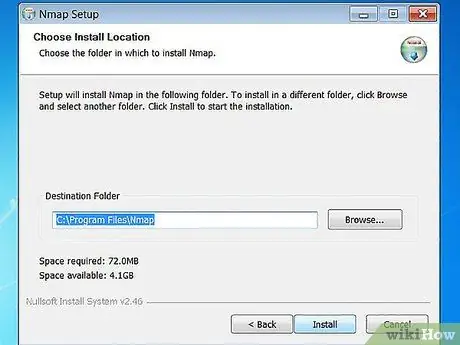
If you don't want Zenmap's graphical interface, you can uncheck the Nmap installation process
For Mac OS X - Download the disk image file (a computer file that has the contents and structure of a disk volume) Nmap. This file can be obtained for free from the developer's website Nmap. It is recommended that you directly download the Nmap installer file from the developer's website to avoid viruses or fake files. Use the installation files contained in the disk image file to install Nmap on the computer. Nmap requires OS X version 10, 6 or later.
Step 2. Open the command line
The Nmap command is run from the command line and the scan results are displayed below the command. You can use variables to modify the scan. You can run a scan from any folder on the command line.
-
For Linux - Open Terminal if you are using the GUI for your Linux distribution. The terminal location varies depending on the type of Linux distribution.

Run a Simple Nmap Scan Step 9Bullet1 -
For Windows - You can open a Command Prompt window by pressing Windows key + R and entering "cmd" in the Run field. Windows 8 users can press Windows key + X and select Command Prompt from the menu. You can run an Nmap scan from any folder.

Run a Simple Nmap Scan Step 9Bullet2 -
For Mac OS X - Open the Terminal application which is in the Utility subdirectory of the Applications folder.

Run a Simple Nmap Scan Step 9Bullet3
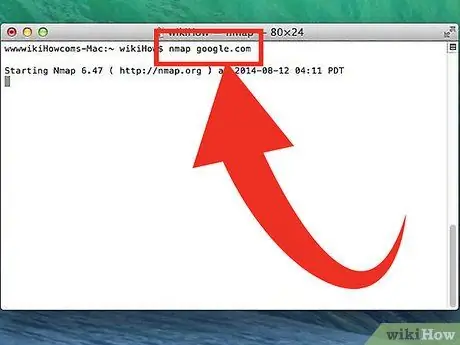
Step 3. Run a scan on the target port
To run a basic scan, type
nmap
. This will ping the target and scan the port. This scan is easy to detect. The scan result will be displayed on the screen. You may have to move the window up to see the entire scan.
Depending on the intensity and target of the scan, running an Nmap scan may violate the rules set by your internet service provider and could get you into trouble. We recommend that you check local regulations and the contract of the internet service provider you are using before running an Nmap scan on targets originating outside your network
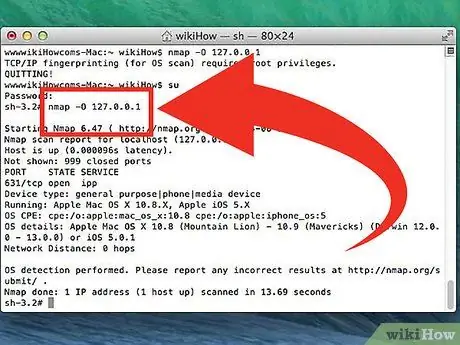
Step 4. Run the modified scan
You can use command variables to change the scan parameters so that the search results will have more or less information. Changing the scan variable will change the level of interference generated by the scan. You can add multiple variables by putting a space between each variable. The variable is put before the target:
nmap
- -sS - This is a SYN scan done silently. This scan is more difficult to detect than a standard scan. However, the scan will take longer. Many modern firewalls can detect "-sS" scans.
- -sn - This is a ping scan. This scan will disable port scanning and only check for hosts that are logged into the network.
- -O - This is an operating system scan. This scan will attempt to determine the target operating system.
- -A - This variable activates several commonly used scans: OS detecting, version detection, script scanning, and traceroute.
- -F - This scan activates fast mode and reduces the number of ports scanned.
- -v - This scan will show more information in the search results so you can understand them more easily.
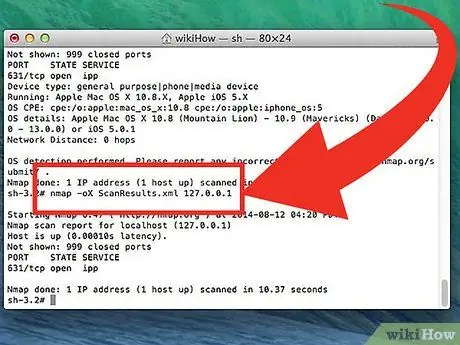
Step 5. Convert the scan results to an XML file
You can convert the scan results to an XML file so you can view them easily in any browser. To do this, you must use the variable -oX and also specify the XML file name. The following is an example of the command used to convert the scan results to an XML file:
nmap -oX Search Result.xml
The XML file will be saved in the folder where you saved the work file
Tips
- If the target is not responding, try adding "-P0" to the scan. This will force Nmap to start scanning even if the program thinks that the selected target cannot be found. This method is useful for computers that are blocked by a firewall.
- Do you want to know the progress of the scan? While the scan is in progress, press the space bar or any key to view the progress of the Nmap scan.
- If the scan takes a very long time (twenty minutes or more), try adding "-F" to the Nmap scan to make Nmap scan only frequently used ports.
Warning
- If you run Nmap scans frequently, be prepared to answer your internet service provider's questions. Several internet service providers look at Nmap traffic regularly and Nmap is an easy tool to detect. Nmap is a tool that is known by many and is usually used by hackers. As such, you may be suspected by your internet service provider and will have to explain in detail why you are using Nmap.
- Make sure you have permission to scan the target! Scanning www.whitehouse.gov could get you in trouble. Try scanning scanme.nmap.org if you want to try the Nmap application. This website is managed and maintained by Nmap developers. Therefore, you can scan it without having to worry about getting into trouble.






