- Author Jason Gerald gerald@how-what-advice.com.
- Public 2023-12-16 10:50.
- Last modified 2025-01-23 12:04.
This guide will explain the simple steps for installing the Tor Browser bundle on a Linux computer, and it can be followed in 5 minutes. The Tor Browser bundle is a free and open source program designed to protect your privacy while browsing the internet.
Note: If you've tried the steps below and Tor still doesn't work, your computer or firewall settings might have a problem. To find out how to solve the problem, click here.
Step
Method 1 of 2: Using the GUI
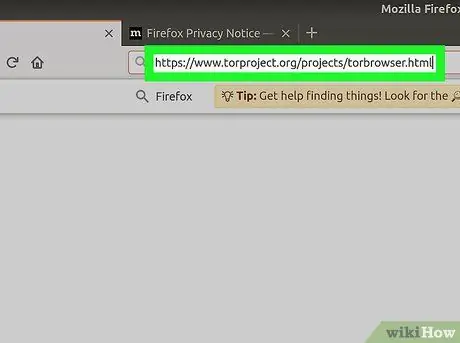
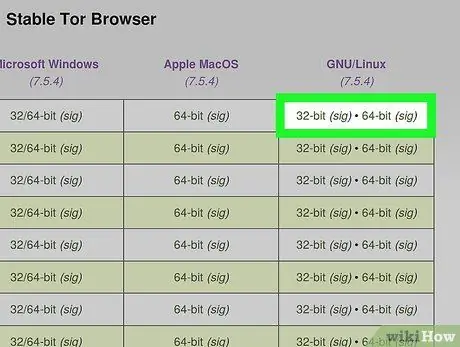
Step 1. Download the Tor Browser Bundle for Linux to the downloads folder on your computer
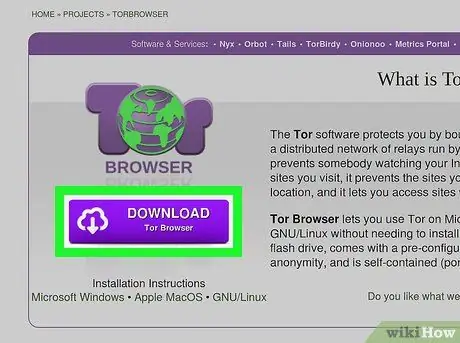
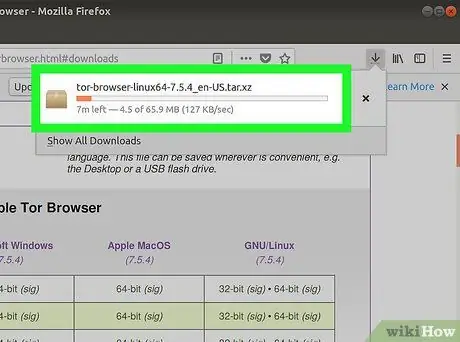
Step 2. Extract the Tor archive
- Open your downloads folder.
- Right-click the file, then select "Extract Here".
Step 3. Start Tor Browser
Click the "start-tor-browser" file in the new folder (tor-browser_en-US)
Step 4. Wait one minute
Tor Browser will display a browser window. Now, you can surf the internet on the open Tor network.
Method 2 of 2: Using the CLI
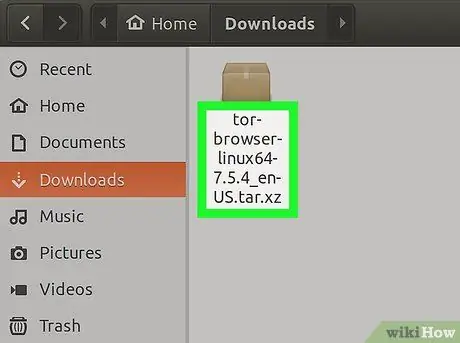
Step 1. Download the Tor package for Linux
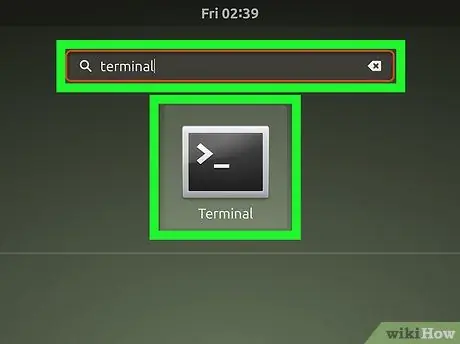
Step 2. Open a Terminal window
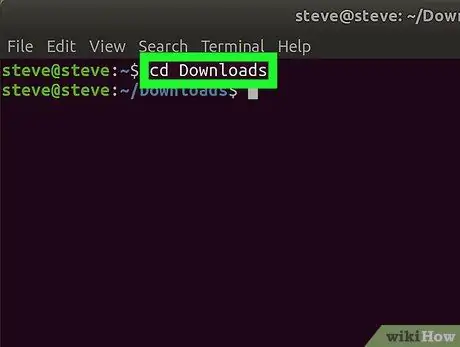
Step 3. Extract the file by running the command tar xzf tor -X. X. X. XX.tar.gz Note: x.x.x.xx is the version of Tor.
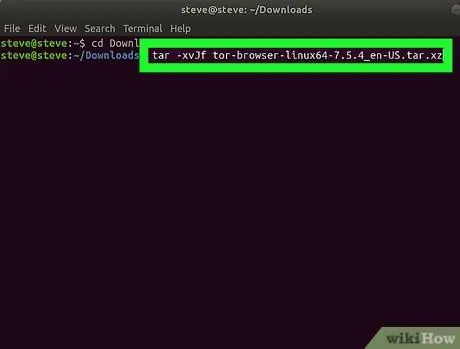
Step 4. Go to the extracted folder with the command cd tor-X. X. X. XX Note: x.x.x.xx is the version of Tor.
Step 5. Perform the configure and make process with the command /configure && make
Step 6. Install and run Tor with the commandsrc/or/torAtaumake installTor
Step 7. Make sure you have Privoxy
To use the newly installed Tor, you must also have Privoxy installed. Unfortunately, unlike Windows or Mac, the Privoxy package is not available for Linux.
Warning
- Read the warning documentation on the official Tor site.
- Keep the following in mind when using Tor. First, not all data traffic will be anonymous after Tor installation. The only data traffic that is made anonymous when Tor is first installed is data traffic from Firefox. This means that you must install a proxy in another program before it can use the Tor network. Second, the Tor button in Firefox will block technologies that can leak identity, such as Java, ActiveX, RealPlayer, QuickTime, and Adobe. To use any of the above add-ons with Tor, you will need to edit the settings file. Third, cookies that existed prior to installation of Tor may leak a user's identity. To ensure user anonymity, delete all cookies before installing Tor. Fourth, Tor encrypts data up to the network exit point. To truly protect data, users must use HTTPS or other trusted encryption. Fifth, users must ensure the integrity of applications downloaded from Tor. Apps can be the cause of identity leaks if a Tor router is hacked.






