- Author Jason Gerald gerald@how-what-advice.com.
- Public 2023-12-16 10:50.
- Last modified 2025-01-23 12:04.
Keeping your computer safe is an important step in protecting your stored personal, business, and financial information. Fortunately, the security process can be done easily if you take the right countermeasures. Using a secure password and verification process will make it difficult for other people or programs to impersonate you and access information on your computer. Protective software also helps make it difficult for hackers, viruses, or malicious programs to get into computers. Also, enable encryption and take precautions to keep your data safe when you use the internet.
Step
Method 1 of 4: Using a Protective Program
Step 1. Install an antivirus program to protect the computer
An antivirus program is a security tool designed to protect your computer from viruses, spyware, malware, and other online threats. A quality antivirus program usually needs to be purchased and installed on the computer.
- Some fairly popular program choices include Avast, AVG, McAfee, and Symantec.
- Set the program to automatically scan for viruses and malware so you can make sure your computer is free of both.
- Some programs can block ads and spam from websites to keep your computer safe while you browse the internet.
Step 2. Activate the firewall to filter information from the internet
A firewall is a program that monitors information coming from an internet connection to a computer so that it can block malicious programs. Open a Control Panel window on the computer and access the “System and Security” menu. Click the “Windows Firewall” shortcut and make sure the feature is enabled.
- The Windows firewall built-in feature is just as powerful as the antivirus program's built-in firewall feature.
- Make sure the computer is connected to the internet network when you activate the firewall for the feature to connect to the internet.
- If you can't find the firewall shortcut, type “firewall” into the search bar in the “System and Security” menu.
Tip:
If you have an antivirus program that includes a firewall feature, use that feature to align with the antivirus program you are running.

Step 3. Clean the computer using a malware removal program
Firewalls and antivirus programs are designed to prevent a computer from becoming infected, but they cannot eradicate a virus or malware that has already infected the computer. Therefore, use an anti-malware program to clean the system after the computer has suffered an attack or infection. Download the program and run periodic scans to check if there are any malicious programs installed on the computer.
- Some popular malware removal programs include Spybot Search & Destroy and Malwarebytes Anti-Malware.
- Schedule periodic scans to check for snooping devices, malware, and viruses.
Method 2 of 4: Encrypting Data
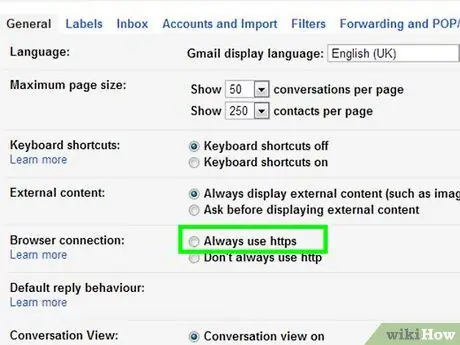
Step 1. Select “Always use https” in Gmail
To make sure your Gmail page always uses a secure HTTPS connection, click the gear icon in the top-right corner of the page. Scroll the menu to the “General” tab. On the menu, select the option to always use an HTTPS connection.
- Gmail settings will be saved so that every time you access the Gmail service, you will use an HTTPS connection.
- Your Gmail account may contain a lot of important and personal information so keep your account secure with an HTTPS connection.
Step 2. Set up Facebook to use an HTTPS connection
To change your Facebook account settings to use an HTTPS connection, click the down arrow icon in the upper right corner of the screen and select “Account Settings” ("Account Settings"). In the account settings menu, click the “Security” option to display a new menu. In the “Secure Browsing” section, check the box labeled “Browse Facebook on a secure connection (https) when possible” (“Browse Facebook using a secure connection [https] if possible”) to change the settings.
Viruses and malware can enter your computer through your Facebook account
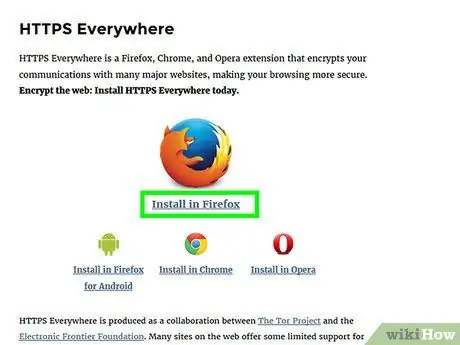
Step 3. Install the HTTPS Everywhere extension on the browser
If you use Google Chrome, Opera, or Firefox as your web browser, you can add an extension that automatically requests an encrypted connection every time you visit any web page. If the page supports HTTPS connections, the browser will automatically use the encrypted connection. Download the extension to add it to your browser.
Visit https://www.eff.org/https-everywhere to download the extension
Tip:
Once installed, make sure the extension is enabled by clicking on its icon in the corner of the browser window.
Step 4. Protect the WiFi connection with a VPN service
If you use a public WiFi connection or someone else's connection, your computer can be compromised by hackers, viruses and malware. A Virtual Private Network (VPN) service encrypts information and keeps your computer safe so you can browse the internet safely.
- You can subscribe to popular VPN services like Tunnel Bear, Cyber Ghost, or ProtonVPN.
- There are many VPN services that offer a monthly subscription fee so you can use the encryption features they offer.
- You can also look for free VPN services that you can use from the internet.
Step 5. Use an HTTPS connection on the website to secure the computer
Hypertext transfer protocol secure (HTTPS) is an encrypted website connection that browsers use when you access and view web pages. You can tell if a site is using that connection if you see "https:" at the beginning of the site's address in your browser's address bar.
Most websites use HTTPS connections to keep your computer safe from virus and malware threats
Method 3 of 4: Setting Up Strong Password Protection
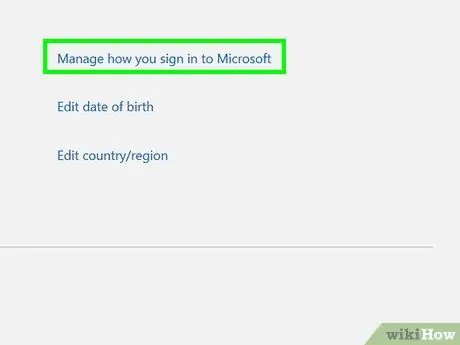
Step 1. Enable the two-step verification option on Windows accounts
Open a web browser and sign in to your account via the Microsoft website. Look for the security settings option at the top of the page and click an option to access the menu. When the additional security menu displays, look for the “Two-step Verification” option. Click the button to activate the option.
- Sign in to your Microsoft account at
- The two-step verification system adds another way for you to verify that you are the one using your account, increasing the level of computer security even more.
- You don't need to use Outlook or any other Windows application to set up a two-step verification system.
Tip:
To add a second verification, you'll need a device or email account so Microsoft can send you a code to prove that you're using or accessing your account. Enter a phone number if you'd like to receive the code by text message or enter an email address if you'd like to receive it by email.
Step 2. Download an authenticator app to secure the apps you use
Install the app on your smartphone or tablet so you don't have to receive a code via text message or email every time you need to verify that you're accessing the app or account. Add all the apps you use to the authenticator app so you can easily self-verify and secure all apps.
- Popular authenticator apps include Google Authenticator, Authy, and LastPass.
- Add social media accounts to the authenticator app to increase the level of security.
Step 3. Use a password manager program to save your passwords
Programs like this not only store and track passwords, they also allow you to create and use a strong and unique password entry every time you register on a new website or application. When you sign in to your account, you can take the password from the program, copy it, and paste it into the login field.
- Some password management programs come with browser extensions that can automatically fill in password fields.
- Some popular password management programs include: LastPass, 1Password, and Dashlane.
- You may need to pay a monthly or yearly subscription fee to download some password manager programs.
Step 4. Add the phone to Google account to enable two-step verification
Google uses a two-factor authentication system known as “2-Step Verification” to make accounts more secure. Open the account security settings through the browser and add your phone to the account to activate the system. You will receive the code via text message, phone call, or authenticating app.
Download the Google Authenticator app from your device's app store after you've activated the two-step verification system to get a verification code, even when your device isn't connected to the internet
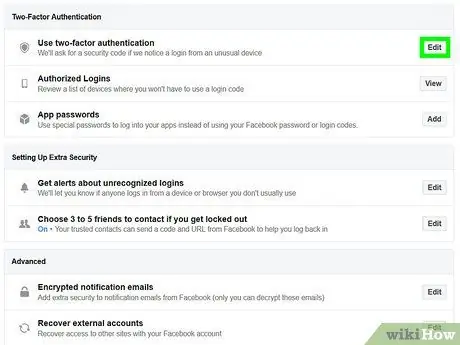
Step 5. Change Facebook settings to enable two-factor authentication
To make your Facebook account more secure, open the "Security and Login" menu in the account settings. Click " Edit " ("Edit") to the right of the " Two-Factor Authentication " option ("Two-Factor Authentication") to specify the process of receiving a second authentication. You can receive the code via text message or authenticating application.
Your Facebook account is full of personal information that needs to be protected. On the other hand, accounts can also be an entry point for hackers or malware to break into your computer
Method 4 of 4: Following Safe Habits
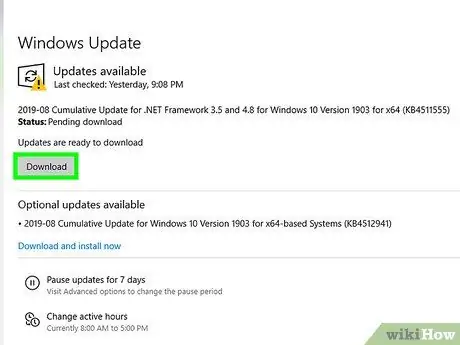
Step 1. Make sure your computer's operating system is always up to date
It is important that you make sure your computer has all the latest equipment and updates to keep it safe. Open the “Windows Update” option via Control Panel and click “Check for Updates”. Select the option to install any available updates.
- Some updates can take up to an hour to complete, especially if you haven't updated your operating system in a while.
- Restart the computer after the operating system has finished updating for the update to take effect immediately.
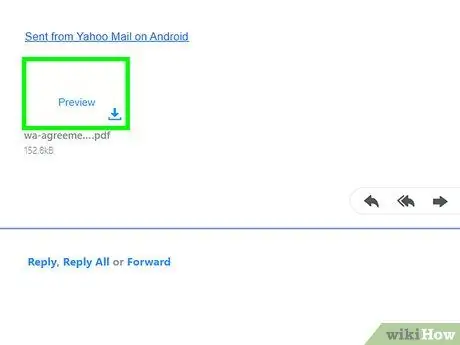
Step 2. Scan email attachments before you open them
Even if the email comes from someone you know, it's possible that the email is a form of a tactic known as “spear phishing”. In this tactic, the sender pretends to be a contact in order to gain access to your email account and computer. Right-click the attachment and select the option to scan the file manually to make sure it's not malicious.
Tip:
Never open attachments to emails from people or companies you don't know.
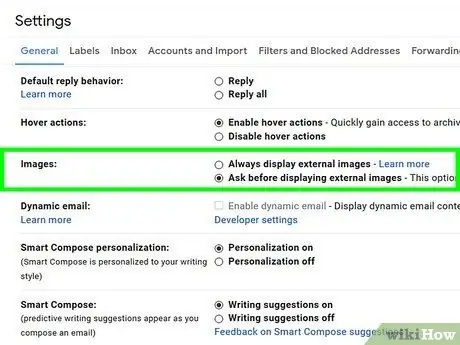
Step 3. Disable images in emails as an added security measure
Malicious programs can take advantage of loopholes to access email accounts and computers. To avoid unwanted programs, disable images in received messages. Go to the account settings menu and select the option that asks you for approval before the image is displayed in the email.
In Gmail, click the settings option in the upper-right corner of the screen. Select the email settings menu and click the box next to “Ask before displaying external content”
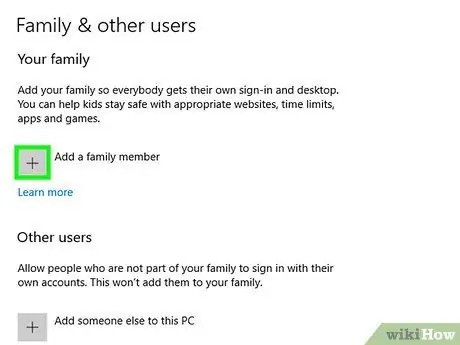
Step 4. Use a nonadministrator Windows account to block malware
If you set up your computer without changing any settings, you may be using an administrator account that puts your computer at risk of attack. Select the “Manage another account” option on the “User Accounts” menu and create a new account. Select “Standard user” when you create an account.
The use of a standard account provides an additional level of security on the computer
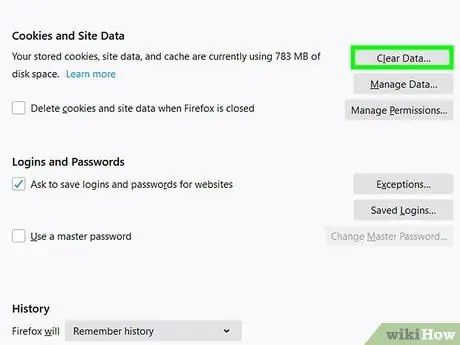
Step 5. Clear any cookies you don't want or need from your browser
Cookies are a “way” for websites to store information about you and your browser to make browsing the site easier and more convenient. However, cookies can also be misused by hackers or malicious programs. Go to browser settings menu and clear any cookies you don't want/need.
Storing cookies for certain sites may be useful so that you don't have to re-enter your information on frequently visited sites
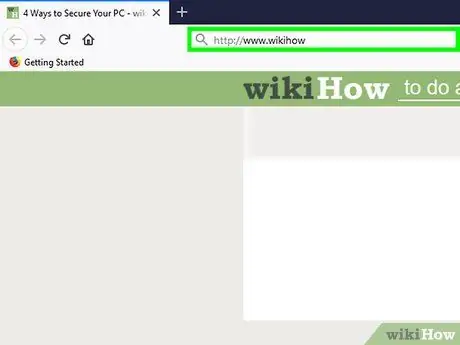
Step 6. Avoid websites that do not have “HTTPS” in their address
If a website looks suspicious or asks you to enter personal information, don't visit the site to protect your computer from being hacked or hacked. One clear sign that a website is not secure is the absence of “HTTPS” in its web address.






