- Author Jason Gerald gerald@how-what-advice.com.
- Public 2024-01-19 22:11.
- Last modified 2025-01-23 12:04.
Monitoring network traffic isn't just for big business; Small businesses can do it too. Monitoring network traffic in a small business or family business has many benefits and can produce surprising results. We recommend that you have a basic understanding of networks and protocols before monitoring your network traffic.
Step
Step 1. Download the Wireshark program
The program was previously called Ethereum, and can be downloaded at https://www.wireshark.org/. This is the most popular network monitoring program used by many professionals in this field around the world. You can even get certified as an Official Wireshark Certified Network Analyst.
Step 2. Install Wireshark and WinPcap
WinPcap is used to help capture network packets.
Step 3. Open Wireshark
Click the " Capture " menu, then click " Interfaces " (interfaces). A small window showing all your network interfaces will appear. If you are using network traffic, you will see packets popping up.
Step 4. Click the "Start" button to start recording network traffic
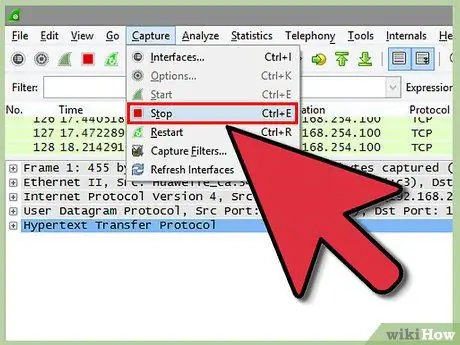
Step 5. Stop monitoring the network
Visit the "Capture" menu again and click "Stop." Network traffic will be easier to analyze if it is paused. However, you can let the program continue monitoring traffic while analyzing packets.
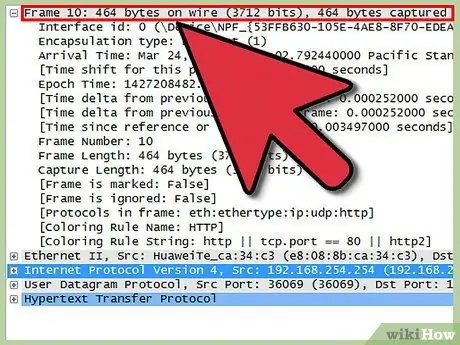
Step 6. Check the information of each package
Each row represents a package, and there are six columns that provide information about that package.
- The column number indicates the order in which the packets started recording network traffic. This way, you get a reference number so you can easily identify a particular package.
- The time listed is the time in seconds to 6 decimal places, when the packet is received after you start recording network traffic.
- The sources listed include the Internet Protocol (IP) address from which the packet originated.
- The destination IP record is where a particular packet goes.
- The protocol the packet uses. The most frequently used protocols are TCP, UDP and
- Information that includes what happened to the packet, either ongoing traffic or an acknowledgment of receipt of the packet.
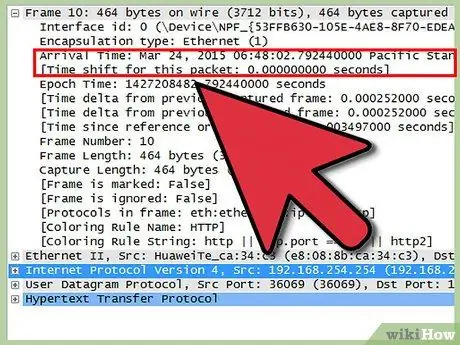
Step 7. Analyze the package list
You can monitor many different things with WireShark.
- Check if any unwanted packets are received or sent on your computer. This includes unwanted people on the network, or even programs that shouldn't be using network traffic.
- Monitor how often programs use your network. For example, how often does Windows Update check for updates?
- Find out what programs are wasting network traffic and overloading the network.






