- Author Jason Gerald gerald@how-what-advice.com.
- Public 2024-01-15 08:07.
- Last modified 2025-01-23 12:04.
Spyware is a type of malicious software that makes changes to your device without your knowledge, such as advertising products, collecting personal information, or changing device settings. If you notice a decrease in device or network performance, notice changes to your browser or other unusual activity, your computer may have been infected with spyware.
Step
Method 1 of 4: Detecting and Removing Spyware on Android
Step 1. Identify suspicious activity on the device
If you feel that the network speed is often slow, or you receive messages that are suspicious or from strangers, your phone may be infected with spyware.
If you receive an inappropriate message or ask you to reply to a message with a specific code, this indicates that your phone is infected with spyware
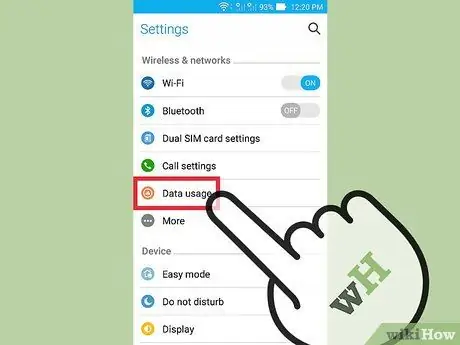
Step 2. Check your data usage
Open the "Settings" app and tap the "Data Usage" option. You can move the screen down to see the amount of data used by each app. High data usage indicates that your phone may be infected with spyware.
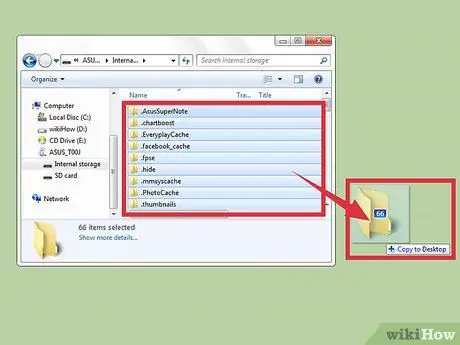
Step 3. Back up your data
Connect the phone with the computer via a USB (Universal Serial Bus) cable. After that, copy and paste your phone data to your computer, such as photos and contact info, to back it up.
When backing up data from your phone to your computer, your computer will not be exposed to spyware because your device and computer have different operating systems
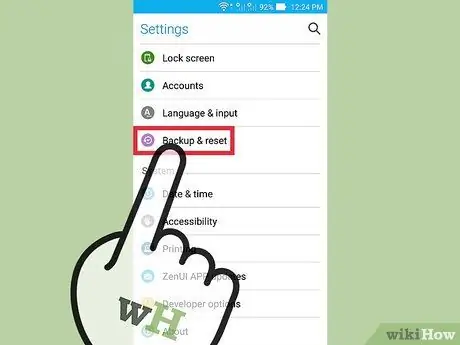
Step 4. Open the “Settings” app and tap on the “Backup & Reset” option (Backup and Reset)
This will open a menu containing various restore options, such as restoring the phone to factory settings.
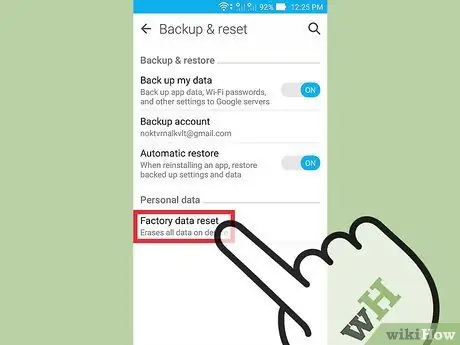
Step 5. Tap on “Factory data reset” (Factory data reset)
It's at the bottom of the "Backup & Restore" menu.
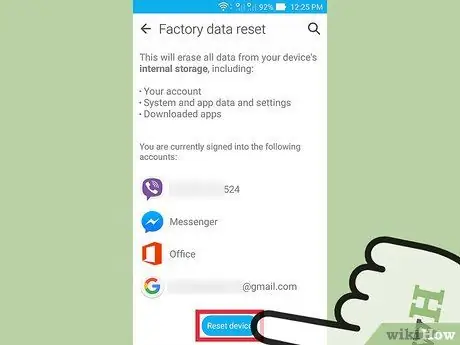
Step 6. Tap on “Reset phone” (Reset Phone)
Your phone will turn off and on (restart) automatically and delete all apps and data, including spyware stored on the phone. After that, the phone will be returned to factory settings.
Restoring the phone to factory settings will erase whole data stored on the phone. Therefore, you should first back up your data before performing this step.
Method 2 of 4: Using HijackThis for Windows-Based Computers
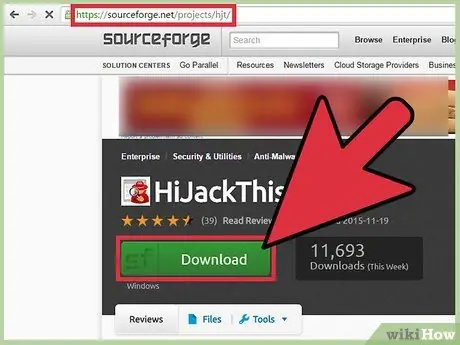
Step 1. Download and install HijackThis
HijackThis is a diagnostic tool for Windows that is used to detect spyware. Double-click the HijackThis installer file to install it. Once installed, run this software.
Other free software, such as Adaware and MalwareBytes, have the same functionality as well
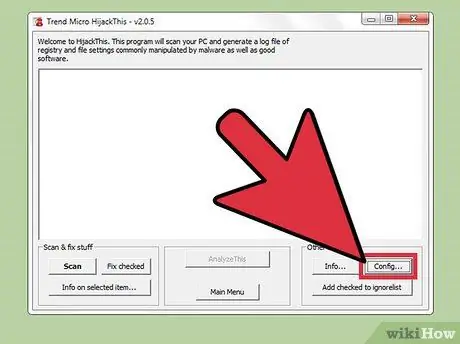
Step 2. Press the “Config…” button
It's in the lower-right side of the window under the “Other Stuff” heading. Clicking the button will open a window with a list of options for the program.
- In this window you can enable or disable important options, such as file backup. It's a good idea to make it a habit to back up your data when trying to delete files or software. If you make a mistake, the lost data can be recovered. Backed up data takes up very little hard disk free space. However, the data can be deleted at any time by deleting it from the folder where the backup data is stored.
- Note that the “Make backups before fixing items” option is enabled by default.
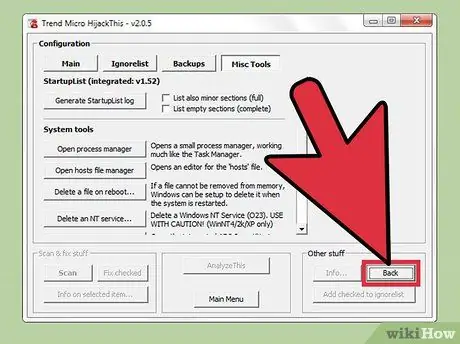
Step 3. Press the “Back” button to return to the main menu
This button will replace the “Config…” button when the configuration window opens.
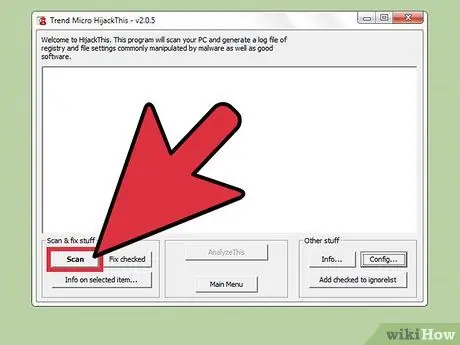
Step 4. Press the “Scan” button
This button is in the lower-left side of the window and will generate a list of files that could potentially be exposed to spyware. It is important to note that HijackThis performs a brief scan of the suspected locations for malicious software. Not all scan results are malicious software.
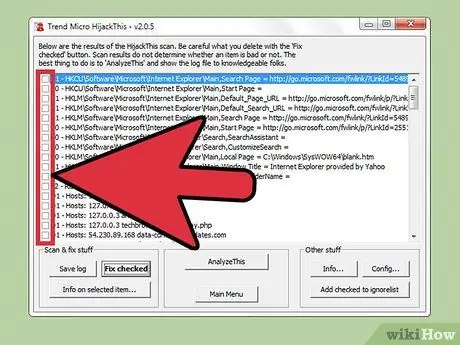
Step 5. Check the box next to the suspicious files and click “Info on selected item…”. This will display information about the file and why HijackThis classified it as suspicious in a separate window. Close the window when you are done checking the scan results.
The information displayed usually includes the location of the file, the function of the file, and the steps to be taken to fix it
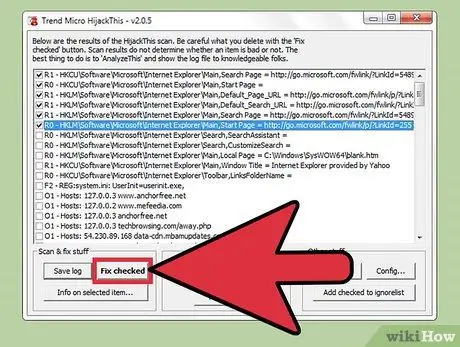
Step 6. Press the “Fix checked” button
It's in the lower-left side of the window. After pressing the button, HijackThis will repair or delete the selected file, depending on the diagnosis.
- You can repair multiple files at once by checking the box next to the files.
- Before making any changes, HijackThis will back up the data by default. That way, you can undo changes if you make a mistake.
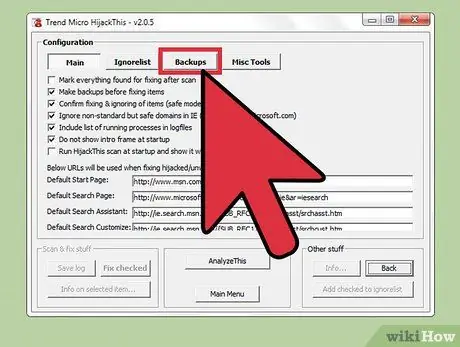
Step 7. Restore files from backup data
If you want to undo the changes made by HijackThis, press the “Config” button at the bottom right of the window and click the “Backup” button. Select the backup file (marked with the date and timestamp when the file was backed up) from the list and press the “Restore” button.
The backup data can still be accessed on different HijackThis usage sessions. You can close HijackThis and restore files from a backup whenever you want
Method 3 of 4: Using Netstat for Windows-Based Computers
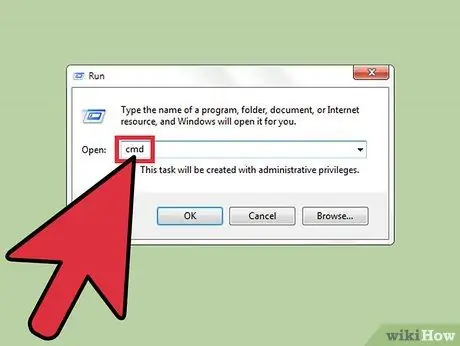
Step 1. Open a Command Prompt window
Netstat is a built-in Windows tool that helps you detect spyware or other malicious files. Press Win + R to run the program manually and enter "cmd" in the search field. The Command Prompt allows you to interact with the operating system using text commands.
This step can be used if you don't want to use third-party software or want to manually remove malicious software
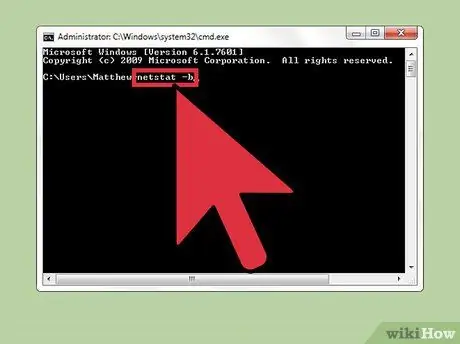
Step 2. Enter the text “netstat -b” and press Enter key
This will display a list of programs that are using the network or monitoring ports (listening ports or processes connected to the internet).
In the "netstat -b" command, the letter "b' stands for "binaries." This command will display the "binaries" (executable programs or the program that is currently executing) and their connections
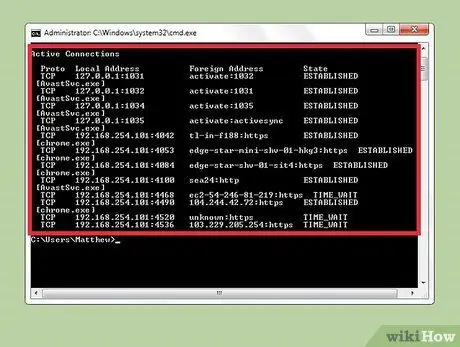
Step 3. Identify suspicious processes
Look for an unknown process name or port usage. If you don't know the function of an unknown process or port, search the internet for information. You will meet people who have encountered this process and they can help you determine whether this process is dangerous or not. If the process is harmful to your computer, you should immediately delete the file that is running it.
If you are not sure whether the process is malicious or not after searching the internet for the information, you should not delete or move it. Modifying or deleting the wrong files can cause other software to crash
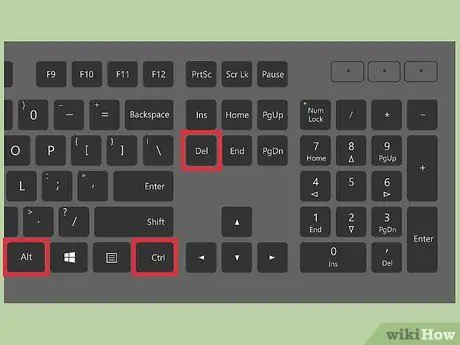
Step 4. Press Ctrl. key + Alt + Delete simultaneously.
This will open the Task Manager which shows all the processes running on the computer. Move the window down to look for the suspicious process name you found in the Command Prompt.
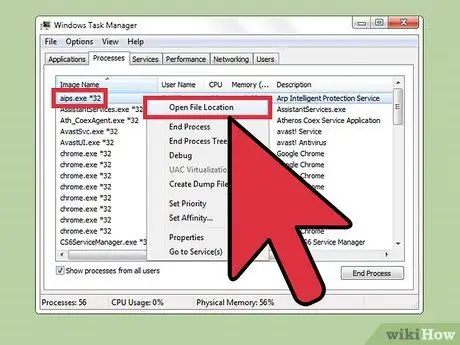
Step 5. Right click the process name and select “Show In Folder”
This will open the folder where the suspicious file is located.
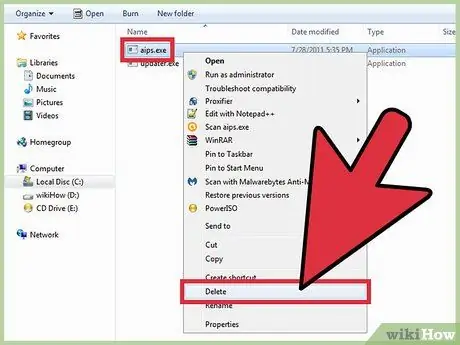
Step 6. Right-click the file and select “Delete”
This will move the malicious files to the Recycling Bin. The process cannot be executed from this place.
- If you get a warning that the file can't be deleted because it's in use, reopen Task Manager, select a process, and hit the "End Task" button. This will disable the process. After that, you can move the file to the Recycling Bin.
- If you delete the wrong file, you can double-click the Recycling Bin to open it. After that, click and drag the file to another folder.
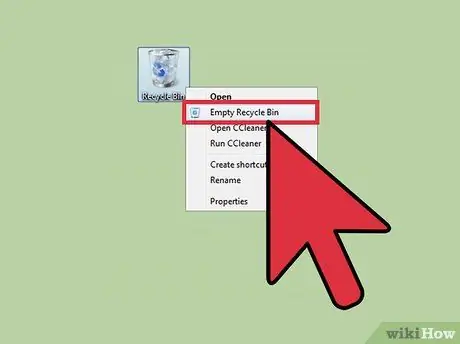
Step 7. Right-click the Recycling Bin and select “Empty Recycling Bin”
This will permanently delete the file.
Method 4 of 4: Using Terminal for Mac
Step 1. Open Terminal
Using the Terminal, you can run a diagnostic tool that can detect spyware on your computer. Go to “Applications > Utilities” and double-click Terminal to launch it. This program allows Ada to interact with the operating system using text commands.
To find this program, you can also search for “Terminal” in Launchpad
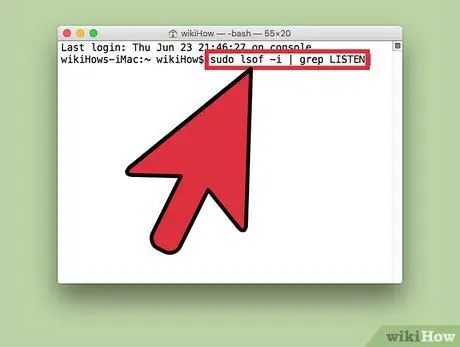
Step 2. Enter the text “sudo lsof -i | grep LISTEN” and press Return key
This will instruct the computer to display a list of processes and their network information.
- The "sudo" command allows the root user (the user who has the authority to open and modify files in the system area) to execute commands. Using this command, you can view system files.
- The "lsof" command is short for "list of open files". This command allows you to see the processes running on the computer.
- The "-i" command requires Terminal to display a list of files that use the network. Spyware will attempt to use the network to communicate with foreign devices or computers from outside your network.
- “grep LISTEN” is used to instruct the operating system to filter files that monitor or use ports. Spyware usually uses or monitors ports to work.
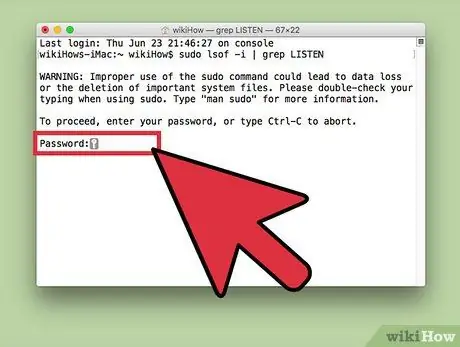
Step 3. Enter the computer administrator password and press the Return key
Even if it is not displayed in Terminal, the password will still be entered to access the administrator account. It is important to enable the 'sudo' command.
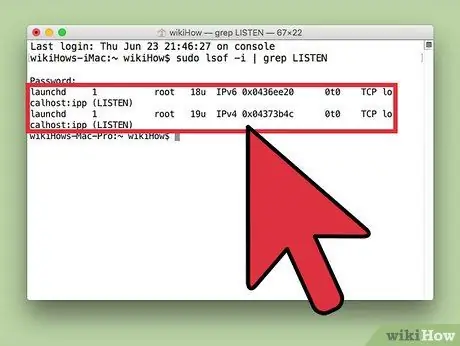
Step 4. Identify suspicious processes
Look for an unknown process name or port usage. If you don't know the function of an unknown process or port, search the internet for information. You will meet people who have encountered this process and they can help you determine whether this process is dangerous or not. If the process is harmful to your computer, you should immediately delete the file that is running it.
If you are not sure whether the process is malicious or not after searching the internet for the information, you should not delete or move it. Modifying or deleting the wrong files can cause other software to crash
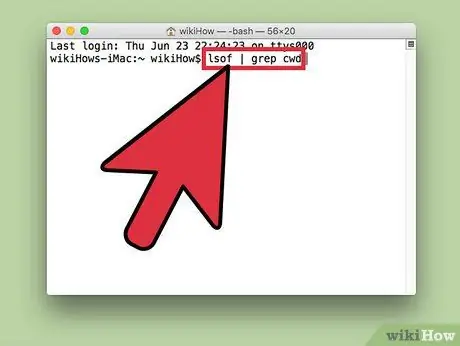
Step 5. Enter “lsof | grep cwd” and press Return key
This will display the folder where the process is stored on the computer. Find the malicious process on the list and copy its location.
- "cwd" stands for current working directory (the folder where the process is running).
- To make it easier to find processes in the list, you can run this command in a new Terminal window by pressing Cmd + N while using Terminal.
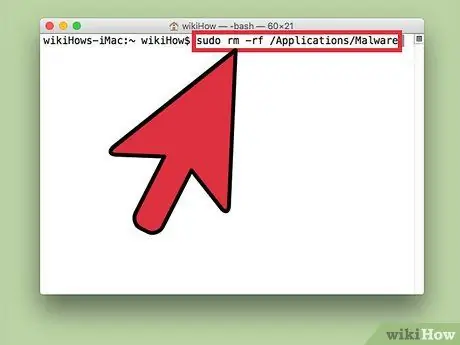
Step 6. Enter “sudo rm -rf [file location]” and press Return key
Paste the process location that you have previously copied into brackets (typed without brackets). This command will delete the files in that location.
- ”rm” is short for “remove” (remove).
- Make sure you really want to delete the file because you can't recover the file after deleting it. We recommend that you use a Time Machine program to back up your data before performing this step. Go to “Apple > System Preferences > Time Machine” and select “Backup”.
Tips
- If you are having trouble understanding the HijackThis scan results, press the “Save Log” button to save the scan results as a text file. After that, upload this file to the HijackThis forum for help.
- Ports 80 and 443 are the ports commonly used to surf the internet. Although they can be used by spyware, these two ports are often used by other applications. As such, it's more likely that spyware won't use this port.
- After detecting and removing spyware, we recommend that you change the passwords of all accounts that you normally access on your computer, such as social media accounts and bank accounts. It's always better to be careful than sorry.
- Some mobile apps advertised as spyware removers for Android may be unreliable or may even steal and corrupt your data. Restoring your mobile device to factory settings is the best way to ensure that your mobile device is free of spyware.
- You can also factory reset iPhone to remove spyware. However, iPhones are usually not susceptible to spyware unless you jailbreak your iPhone.
Warning
- Be careful when deleting unknown files. Deleting files stored in the “System” folder in Windows can damage the operating system and require you to reinstall Windows.
- It's also a good idea to be careful when deleting files using Terminal on a Mac. If you suspect certain processes, you should first look for information about these processes on the internet.






