- Author Jason Gerald gerald@how-what-advice.com.
- Public 2023-12-16 10:50.
- Last modified 2025-01-23 12:04.
The best way to make sure your database is safe from hacker attacks is to think like a hacker. If you are a hacker, what kind of information are you looking for? How to get that information? There are different types of databases and different ways to hack them, but most hackers will try to find the root password or run known database exploits. You can hack databases if you are familiar with SQL statements and understand database basics.
Step
Method 1 of 3: Using SQL Injection
Step 1. Find database vulnerabilities
You must understand database statements to be able to use this method. Go to the database web login screen in your web browser and type ' (single quotes) into the username box. Click “Login.” If you see an error message that says “SQL Exception: quoted string not properly terminated” or “invalid character,” it means that the database is vulnerable to SQL.
Step 2. Find the number of columns
Return to the database login page (or any other URL ending in “id=” or “catid=”) and click on the browser address box. At the end of the URL, press the space bar and type
order by 1
then press Enter. Increase the number to 2 and press Enter. Keep adding numbers until you get an error message. The column number is actually the number entered before the number that generated the error message.
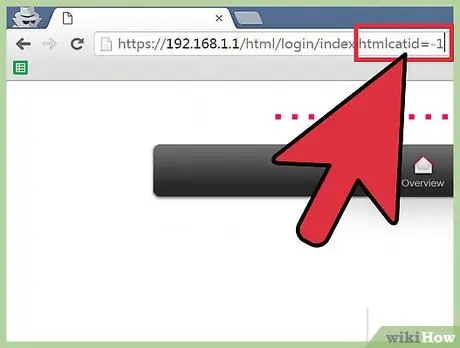
Step 3. Find the column that accepts the request (query)
At the end of the URL in the browser address box, change
catid=1
or
id=1
Becomes
catid=-1
or
id=-1
. Press the space bar and type
union select 1, 2, 3, 4, 5, 6
(if there are 6 columns). The numbers must be in order to the total number of columns, and each number separated by a comma. Press Enter and you will see the numbers for each column that accepted the application.
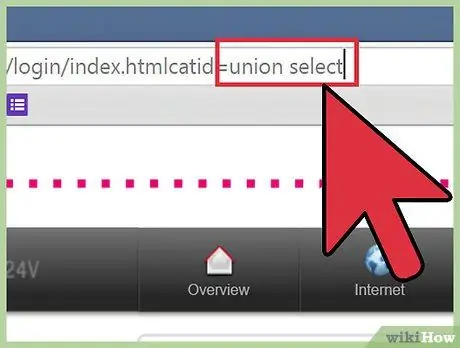
Step 4. Insert the SQL statement into the column
For example, if you want to know who the current user is and put the injection in column 2, remove all text in the URL after id=1 and press the space bar. After that, tik
union select 1, concat(user()), 3, 4, 5, 6--
. Press Enter and you will see the current database username on the screen. Use the desired SQL statement to return information, such as a list of usernames and passwords to hack.
Method 2 of 3: Hacking Database Root Password
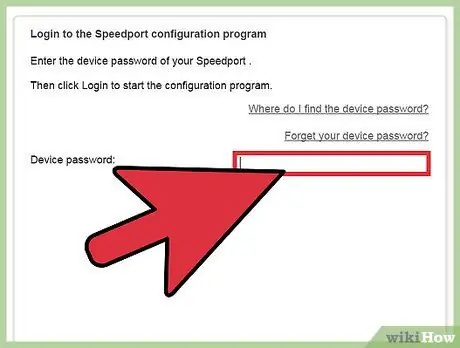
Step 1. Try logging in as root with the initial (default) password
Some databases do not have an initial root (admin) password so you may be able to clear the password box. Some databases have initial passwords that can be obtained easily by searching the technical assistance service forum of the database.
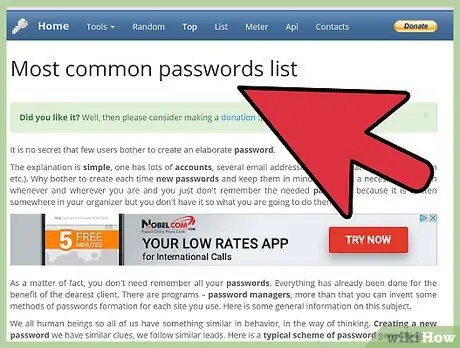
Step 2. Try a commonly used password
If the admin locks the account with a password (most likely), try the usual username/password combination. Some hackers post lists of passwords to public means which they hack using audit tools. Try different username and password combinations.
- A trusted site that has a list of associated passwords is
- Trying one password at a time can take some time, but it's worth trying before resorting to more drastic methods.
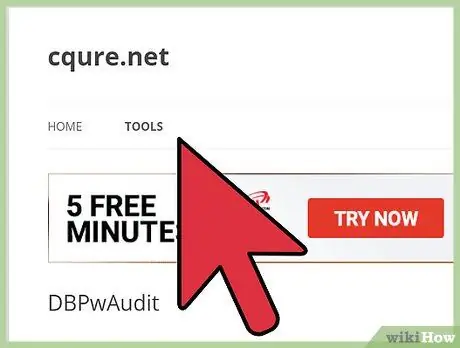
Step 3. Use audit tools
You can use various devices to try thousands of word combinations in the dictionary and brute force letters/numbers/symbols until the password is cracked.
-
Tools such as DBPwAudit (for Oracle, MySQL, MS-SQL and DB2) and Access Passview (for MS Access) are popular password audit tools and can be used for most databases. You can also search for the latest password audit tools specific to your database via Google. For example, try searching
password audit tool oracle db
- if you want to hack Oracle database.
- If you have an account on the server that hosts the database, you can run a hash cracker program such as John the Ripper on the database password file. The location of the hash file depends on the associated database.
- Download programs only from trusted sites. Research the device carefully before use.
Method 3 of 3: Running the Database Exploit
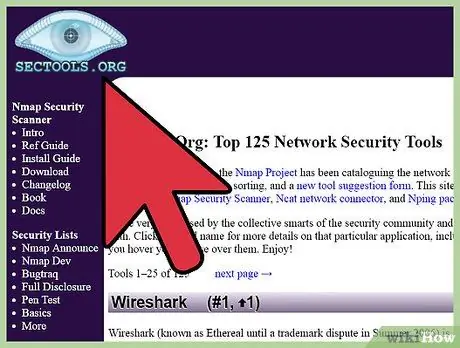
Step 1. Find an exploit to run
Secttools.org has been documenting security tools (including exploits) for over 10 years. These tools are generally trusted and widely used by system administrators around the world for security system testing. Look at the “Exploitation” database on this site or other trusted sites for tools or other text files that help you exploit weak points in the database security system.
- Another site that documents exploits is www.exploit-db.com. Visit the site and click the Search link, then search for the type of database you want to hack (for example, “oracle”). Type the Captcha code in the given box and do a search.
- Make sure you research any exploits you want to try to find out how to work around any problems that could occur.
Step 2. Find vulnerable networks using wardriving
Wardriving is driving (or cycling, or walking) around an area while running a network scanning device (such as NetStumbler or Kismet) to look for weakly secure networks. This method is technically illegal.
Step 3. Use database exploits from weak security networks
If you're doing something you shouldn't be doing, it's best not to do it from your private network. Use the open wireless networks found while wardriving and run the exploits that have been researched and selected.
Tips
- Always keep sensitive data behind a firewall.
- Make sure you protect the wireless network with a password so wardrivers can't use your home network to run the exploit.
- Ask for tips from other hackers. Sometimes, the best hacking science is not disseminated on the internet.
Warning
- Understand the laws and consequences of hacking in your country.
- Never try to gain illegal access to machines from your own network.
- Gaining access to a database that is not yours is illegal.






