- Author Jason Gerald gerald@how-what-advice.com.
- Public 2023-12-16 10:50.
- Last modified 2025-01-23 12:04.
The internet was created for convenience, and not security. If you surf the internet as much as the average person, chances are many people can track your surfing habits through spyware, scripts, and even cameras! With this information, anyone in the world can find out who you are, where you live, and other important personal information.
There are two ways to track other people on the internet:
- By placing malware directly on the computer.
- By listening to what is exchanged using remote servers from any part of the network.
Step
Method 1 of 2: Avoiding Malware
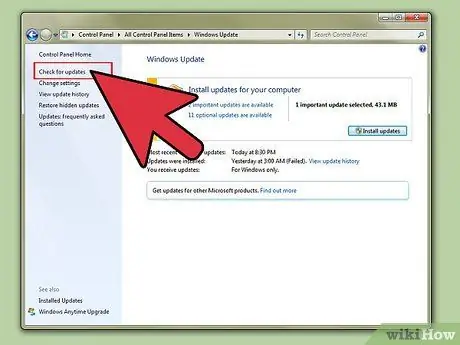
Step 1. Update the operating system (operating system / OS)
The easiest way for other people to track and record everything about you is to install spyware/virus or auto-break into your computer. By regularly updating the computer's OS, the operating system provider can keep the security system up-to-date on critical areas to prevent automated security vulnerability exploits and turn spyware into useless code.
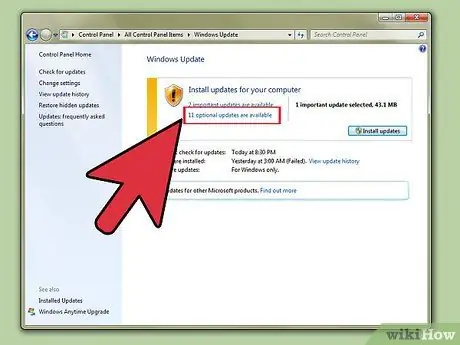
Step 2. Keep the program on its latest version
Program updates are made to improve user convenience and add various features. However, updates are also made to fix bugs in the program. There are many types of lice; some display only visual artifacts, others will prevent you from doing something advertised, and some can be used by remote and automated hackers to take over your computer. Without ticks, ranged attacks can't be done.
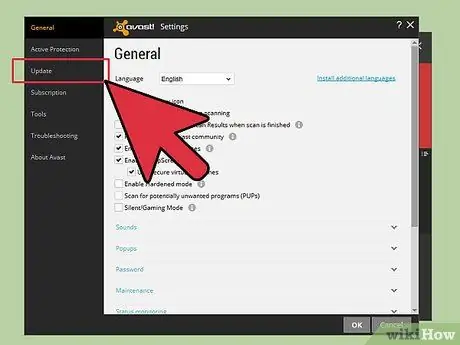
Step 3. Update antivirus regularly and keep it active in MS Windows
If the antivirus signature database is not updated, some viruses can still break through. If the antivirus is not running in the background and does not check the system regularly, uninstall your antivirus program. Note that antivirus programs usually look for viruses, spyware, rootkits, and worms. Specific anti-spyware programs are usually not very effective.
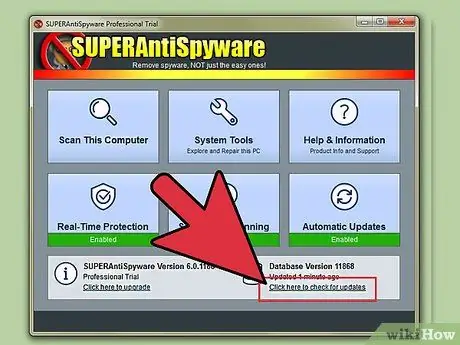
Step 4. Use only one unique antivirus program that is ON
A good antivirus program should monitor the computer very closely. In the best-case scenario, one of the programs will mistake the other antivirus program for a virus. In the worst case, each anti-malware program will block each other's work. If you want to use more than one antivirus, update the database, disconnect the computer from the internet, disable the main antivirus completely and run the second antivirus only in "on-demand" mode. Then, maybe you get a false positive about the main antivirus. Don't worry, this is normal. Launch the main antivirus and you can use the computer as usual. Malwarebytes is a great additional protection program to complement your antivirus.
Step 5. Try not to download anything other than official sites (all OS) or trusted repositories (Linux/BSD/MacOS)
For example, if you want to download VLC Media Player, get it from the official website (search it on Google first or visit www.videolan.org/vlc/). Never use links from any unofficial site, even if the antivirus shows no signs of danger.
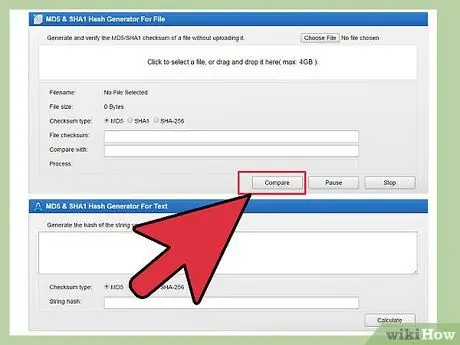
Step 6. Check the binary signature, if possible
You can visit this site to read examples and wiki articles. Please note that md5 is not feasible anymore so we recommend using sha256. Basically, your goal is to create a signature from a file (eg program installer/installer). These signatures are given on official websites or trusted databases. When downloading a file, you can create this signature yourself from the file with a special program. Then, you can compare it to the signature from the site; if they are exactly the same, then you have a good installer. Otherwise, it's possible that you downloaded a fake installer that contains a virus or that the download failed (whatever it was, you'll need to download the file again to be sure). On most Linux distributions, this process is done automatically and in *BSD it uses any package manager without requiring any special action. On Windows, you have to check it manually.
Step 7. Use a firewall
For Linux/*BSD, there are two good firewalls integrated (netfilter/iptables and pf respectively). For MS Windows, you should look for a good firewall. You need to understand that a firewall is similar to a tracker in the middle of a large station containing many trains (network data), platforms (ports), and rails (streams). A buggy can't load itself and needs someone's help (a service or a daemon, i.e. a program running in the background that listens for a specific port). Without someone's help, the service would do nothing, even if the train made it to the platform. Remember, a firewall is not a wall or a gateway, it's a switchman (a firewall can do a lot more than just allow or block the flow of data). However, don't forget that you can't control outgoing connections (unless you block everything or unplug your computer), but you can still log outgoing data. Most spyware finds a way to bypass firewalls, but cannot hide its activity, and you can more easily find spyware that sends data to a remote server on port 933 even if you don't use an IMAP program that finds it, hides in the Internet Explorer process and sends data on port 443 which is used every day. If you can access standard firewalls (netfilter/iptables and PF), simply log any abnormal outgoing data and block all incoming data except existing and associated connections. Don't forget to allow everything on the loopback(lo) device; It is safe and required.
Step 8. Use it only to note if your firewall is stateless
You cannot block incoming data intelligently. Avoid per-app filtering as it is cumbersome, useless, and provides a false sense of security. Most spyware today attaches its malicious code to a trusted application that is thought to be used to access the internet (usually Internet Explorer) and launches with that application. When Internet Explorer tries to connect to the internet, the firewall will ask for your confirmation. If you answer “yes” (yes), the spyware will be able to send anything via ports 80 and 443, along with your real data.
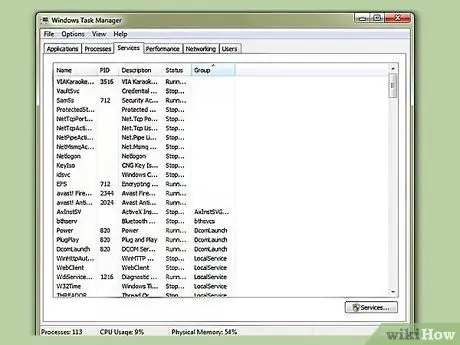
Step 9. Check which services (also known as daemons) are running
As previously mentioned, if there's no one on the platform loading the train, NOTHING can happen. You are not a server; You don't need a service to be able to walk and hear outside! (beware, most Windows/Linux/MacOS/BSD services are REQUIRED and don't listen outside!) If possible, disable useless services or block all data flows on ports connected to the firewall (for example, you can block log in and out on this port if you're not using Windows Shares. Keep in mind, bugs in a service are a wide-open gateway to remotely take over your computer. If the service isn't there or is blocked by a firewall, your computer can't be hacked remotely. You could also try a port scanning program like nmap to determine which ports to block or which services to disable (same result).
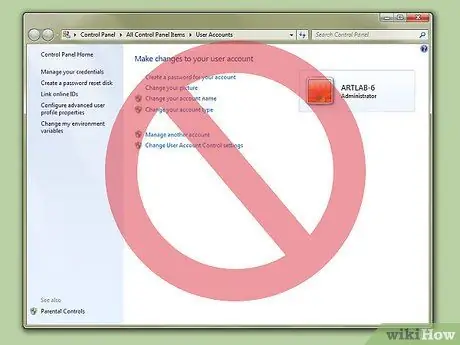
Step 10. Try not to use an admin account
Although it's better in Windows Vista and Seven, if you use an admin account, all software will be able to request admin rights, including malware if launched carelessly. If you're not an admin, spyware will have to try harder to get into your computer. At the very least, if you are a standard user, spyware can transmit your information, but not to other users. Spyware will not be able to use useful parts of the system to transmit data, making it easier to remove from your computer.
Step 11. Switch to Linux if you don't need a computer to play games or use special software
To date, few malware programs are known to attack Linux, and all of them have been disabled long ago thanks to security updates. Binaries are fetched from verified, signed and authentic repositories. You don't need an antivirus and you can get lots of free, open source and quality programs to meet your common needs (Firefox, Chrome, Inkscape, GIMP, Pidgin, OpenOffice, FileZilla, FFmpeg (used in almost every audio/video converter for Windows), Ghostscript (used in every existing PDF converter), XChat, and many more programs that were originally developed on Linux and then imported into Windows because they were so good).
Method 2 of 2: Prevent Others Snooping on Your Connection
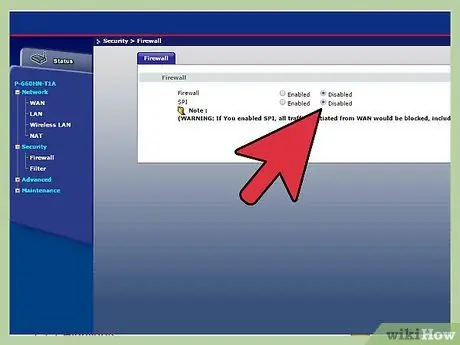
Step 1. Make sure the network cannot be accessed without your knowledge or is disabled
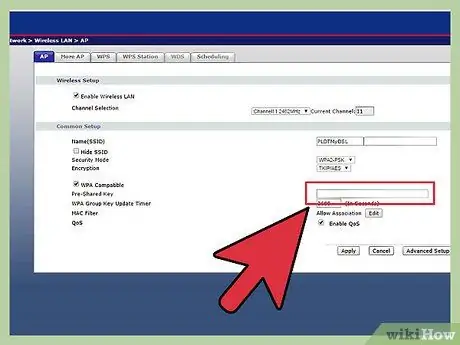
Step 2. Make sure your wireless network is encrypted with minimum WPA-TKIP or maximum WPA(2)-CCMP or WPA2-AES
Currently, the use of WEP encryption or no encryption at all is still dangerous and should not be done.
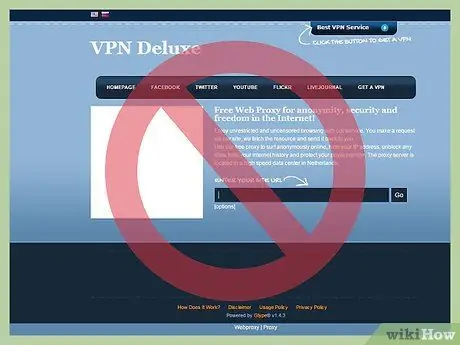
Step 3. Try not to surf through proxies
If you are forced to use a proxy, remember that you are forced to trust a stranger who manages the proxy used. This person can log and store everything you send/receive through their proxy. It can even unencrypt the given protocol you're using (eg HTTPS, SMTPS, IMAPS, etc.) when you're off guard. If so, this person can get your credit card number, and so on. It's much safer to use HTTPS whenever possible than to use dubious proxies.
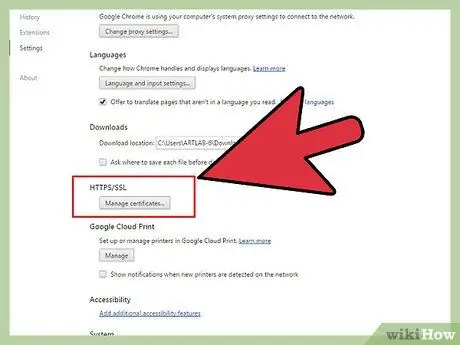
Step 4. Use encryption whenever possible
This is the only way to ensure that no one other than you and the remote server can understand the data being sent and received. Use SSL/TLS whenever possible, stay away from the usual FTP, HTTP, POP, IMAP and SMTP (use SFTP, FTPS, HTTPS, POPS, IMAPS and POPS). If your browser says the certificate is incorrect, leave the site immediately.
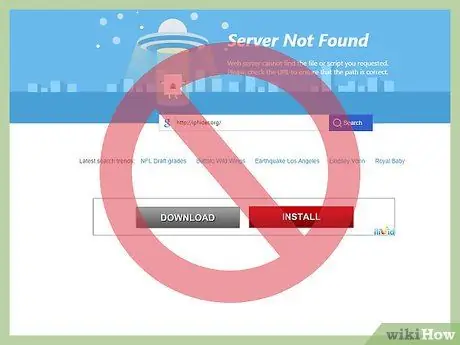
Step 5. Try not to use IP-hide services
This service is actually a proxy. All your data will go through this proxy so they can log and store everything. This service can also provide fake web pages to get your sensitive information and even use it directly on the real site so you don't realize you have given sensitive information to strangers.
Tips
- Don't open emails from strangers.
- Do not open attachments in emails unless they are from a trusted person and the contents are explained
- Web lice are a great way to keep track of which websites to visit. Many extensions can get rid of it like Ghostery for Chrome and Firefox.
- If you're playing an online game that requires an open port, you usually don't need to close it later. Remember, if there is no service, the threat is nil. When exiting the game, no one else listens to the open port as if it were closed.
- One website alone cannot track your IP on another site.
- If you're using a site client, set it up so that the email is displayed in plain text (NOT in HTML). If you can't read the email, then the entire page is an HTML image which is most likely advertising or spam.
- Never put a computer in a DMZ; only people in your network can exploit loopholes. If you are in the DMZ, your network is the internet directly.
- Never use multiple spyware detectors at the same time.
- Your IP is useless to hackers.
- Website owners cannot properly track you using your IP address; in most of the cases, the ISP assigns the IP address dynamically. The IP address will change from time to time and the ISP is the only one who knows who you are. Technically, the ISP will not be able to log and identify everyone.
- As the name implies, an IP address is an address. Just because the address is known, doesn't mean the house is easy to rob! Same thing with IP addresses.
- An open port (inside a firewall) without a bugged service listening behind this particular port is useless to hackers.






